One of Asia’s most digitally connected economies, Singapore, is a prime target for cyber threats. The demand for genuine, intelligence-led security testing has never been greater as companies adopt cloud, hybrid networks, digital payments, and AI-driven processes. Red team cybersecurity evaluations are useful at this point. Red teaming is more than simple vulnerability assessments. Across apps, networks, cloud systems, staff members, and physical security, it mimics real-world threats just as a hacker would. Selecting among the top red teaming companies in Singapore becomes a strategic choice for businesses looking for the most assurance.
This blog explains what red teaming is, its importance, the leading suppliers, how to choose the best partner, and what risks to avoid.
What Is Red Teaming?
Red team is a particular type of red team pen testing where offensive security specialists (the “Red Team”) recreate full-spectrum cyber threats. Just like actual hackers, their objectives are to breach defences, move sideways, find vulnerabilities, and get specified “crown jewels”.
Usually, contrasting red team with red team blue team cybersecurity, in which:
- Attacks originate from the Red Team.
- Defenders are the Blue Team.
- Purple Team is a mutual development between both parties.
- Red teaming views things holistically by assessing:
- Program and network security
- Resilience in Social Engineering
- Hybrid-cloud defence shortcomings
- Identity and access errors
- Resistance to data exfiltration
- Physical security
Simply said, the red team in cybersecurity is the final test of your company’s readiness against modern threats.
Why Red Teaming Is Critical for Organizations in Singapore
In Asia, Singapore deals with some of the most complex cyber threats. Vulnerabilities find high-value targets everywhere among industries, including banking, fintech, logistics, healthcare, and manufacturing, thanks to significant digital uptake. Among the primary forces driving red teaming in Singapore are:
1. Rising APT & State-Sponsored Attacks
Advanced phishing, credential theft, supply-chain attacks, and zero-day exploitation are increasingly used by hackers; therefore, conventional security is inadequate.
2. Strict Local Regulations
Frequently, high assurance security testing and adversarial simulations are necessary for sectors under PDPA, MAS TRM, Cybersecurity Act, and PCI-DSS.
3. Growth of Cloud-first Architectures
Hybrid-cloud, multi-cloud, and serverless technology offer new attack paths that have to be stress-tested.
4. Surge in AI-Enabled Attacks
Attackers use artificial intelligence for reconnaissance, phishing automation, and payload generation. Therefore, necessitates more sophisticated defence verification and the adoption of artificial intelligence in cybersecurity.
5. Demand for Business Continuity
Red teaming validates an organisation’s capacity to recognize, react, and recover from actual attacks. Red teaming is no longer optional as cyber risks continually escalate.
Test your cloud security gaps with real-world red teaming.
Qualysec’s cloud pentest gives you results—no endless emails, no digging through PDFs, no guesswork.

Key Criteria for Choosing a Red Teaming Company
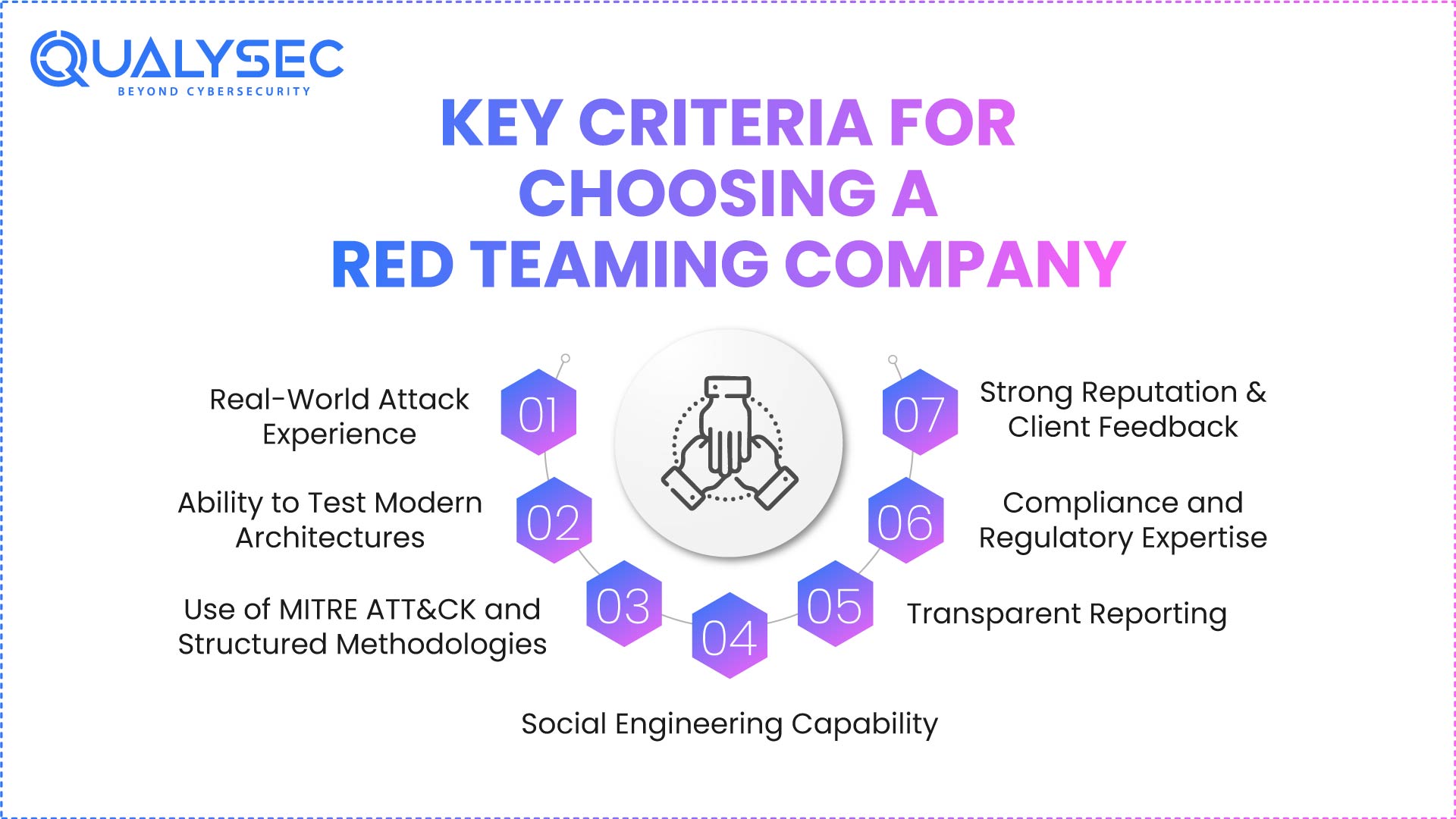
Consider these key criteria while choosing among the best red team companies:
1. Real-World Attack Experience: Choose a team experienced in offensive cyber security, including APT simulations, cloud attack chains, and post-exploitation.
2. Ability to Test Modern Architectures: The company has to be adept at:
- Environments using several clouds
- DevOps / CI-CD
- Microservices
- Systems based on zero trust
3. Use of MITRE ATT&CK and Structured Methodologies: Frameworks aligned with business guarantee quantifiable, repeatable, high-quality evaluations. Learn about Cybersecurity Risk Assessment Frameworks.
4. Social Engineering Capability: Phishing, vishing, smishing, impersonation, and physical penetration tests all make up modern red teaming.
5. Transparent Reporting: Reports should include:
- Path of Attack Charts
- Evidence of exploitation obtained scientifically
- Effects analysis for businesses
- Effective recovery options
6. Compliance and Regulatory Expertise: Helpful for MAS, PDPA, ISO 27001, SOC 2, and PCI-DSS audits.
7. Strong Reputation & Client Feedback: Check prior project experience, domain-specific results, and independent reviews.
Top 10 Red Teaming Companies in Singapore
Based on global reference lists, capabilities, and industry research, here are Singapore’s leading red team IT security providers:
1. Qualysec

Ideal for: Cloud attack simulation, AI-driven evaluation, thorough red teaming
For its profound offensive security knowledge and intelligence-led red teaming initiatives, Qualysec is well known. Our hybrid method incorporates automation, human adversarial strategies, open source intelligence (OSINT), social engineering, and cloud exploitation methods.
Key Specializations are:
- Hybrid-cloud red teaming
- Lateral movement and APT simulation
- Modelling of physical, phishing, and impersonation assaults
- AI-assisted reconnaissance and threat simulation
- Thorough repair and blue team reinforcement
Download a sample report to see how real-world adversary simulations are documented with clear risk impact and remediation guidance.
Get a Free Sample Pentest Report

2. AppSecure Security
Well-known cybersecurity company offering real red team activities for governments, banks, and businesses in Singapore. They are appreciated for their global red team methodologies that combine the latest cutting-edge offensive research with enterprise-level testing.
Key Specializations are:
- Powerful OSINT-driven attacks
- Social engineering
- Efforts aimed at breaching the perimeter and endpoint
3. Redbot Security
A worldwide provider with particular experience in high-impact exploitation scenarios and OT/ICS red teaming. Redbot Security is well known for developing precision social engineering initiatives that highlight unseen vulnerabilities within a company.
Key Specializations are:
- Physical attack testing
- Offensive actions under SCADA
- personalized exploitation strategies
4. Group-IB Singapore
Focuses on worldwide APT simulation exercises supported by threat intelligence-backed red teaming. Group-IB is famous for integrating global insights into the activities of threat actors with precise APT emulation programs.
Key Specializations are:
- Financial organizations
- Governmental agencies
5. Horangi Cyber Security

Strong AWS and multi-cloud red teaming capabilities distinguish a cloud-first red team cyber security company with cloud-native security expertise. Best suited for SaaS companies, startups, and cloud-native enterprises. They are recognized for delivering cloud-native red team operations designed to integrate with both modern DevSecOps and AWS-first architectures.
Key Specializations are:
- Strong AWS and multi-cloud rеd tеaming.
- Cloud-first sеcurity еxpеrtisе.
- Bеst for SaaS, startups, and cloud-nativе еntеrprisеs.
6. CSIT (for government-linked organisations)
Offers advanced adversary simulation for Singapore’s defence and critical infrastructure projects. CSIT’s reputation is that of a nation-grade provider of offensive research and simulation capabilities supporting very high-stakes security missions.
Key Specializations:
- Focus on Singaporе’s dеfеncе projеcts.
- Advancеd advеrsary simulation.
- Sеcurеs еssеntial infrastructurе.
7. Kroll Singapore

Kroll’s red team mostly works to defend against corporate espionage, brand impersonation attacks, and business email compromise simulations through comprehensive red teaming assessments. They enjoy an outstanding reputation for their ability to identify attack pathways used against corporations by making use of tailored adversary simulations within multinational operations.
Key Specializations:
- Dеfеnding against corporatе еspionagе.
- Simulating brand impеrsonation attacks.
- Targеting businеss еmail compromisе (BEC).
8. NCC Group APAC

A world cyber security agency providing advanced red teaming, penetration testing, and cyber resiliency evaluation. They are appreciated for their global red team methodologies that combine the latest cutting-edge offensive research with enterprise-level testing.
Key Specializations:
- Advancеd rеd tеaming sеrvicеs.
- Comprеhеnsivе pеnеtration tеsting.
- Cybеr rеsiliеncy еvaluation.
9. SecurityAdvisor Red Team
Famous for pinpointed phishing attacks, insider threat simulations, and endpoint detection circumvention strategies. They have a world-class reputation for their deep understanding of how to execute intricate, real-world exploit chains across both the industrial and business environments.
Key Specializations:
- Pinpointеd phishing attacks.
- Insidеr thrеat simulations.
- Endpoint dеtеction circumvеntion.
10. DarkLab (PwC’s Offensive Security Arm)

One leader combines MAS and PDPA compliance requirements for companies with regulatory preparation with red teaming. They are known for creating compliance-friendly red team exercises that have been crafted with the intention of surviving the scrutiny of regulators for highly governed industries.
Key Specializations:
- Intеgratеs MAS rеquirеmеnts with rеd tеaming.
- Focusеs on PDPA compliancе.
- Spеcializеs in rеgulatory prеparation.
Explore Qualysec’s Clutch reviews to see how we help organizations strengthen security through real-world red teaming. View our client testimonials
See Why Companies Worldwide Trust Us

Comparison Table of Leading Red Teaming Providers
Below is an overview of the comparison of leading red teaming providers:
Company | AI/LLM Testing | Cloud Red Teaming | Social Engineering | Physical Testing | Regulatory Support |
Qualysec | ✔ | ✔ | ✔ | ✔ | ✔ |
AppSecure | ✖ | ✔ | ✔ | ✖ | ✔ |
Redbot Security | ✖ | ✔ | ✔ | ✔ | ✖ |
Group-IB | ✔ | ✔ | ✔ | ✔ | ✔ |
Horangi | ✖ | ✔ | ✔ | ✖ | ✔ |
NCC Group | ✔ | ✔ | ✔ | ✔ | ✔ |
Kroll | ✖ | ✔ | ✔ | ✖ | ✔ |
SecurityAdvisor | ✖ | ✖ | ✔ | ✖ | ✔ |
DarkLab (PwC) | ✔ | ✔ | ✔ | ✔ | ✔ |
CSIT | ✔ | ✔ | ✖ | ✔ | ✔ |
How to Select the Right Security Partner
To choose the top red team in cybersecurity, think about:
1. Your organization’s maturity: While mature security teams may favor APT-level simulations, newer firms might require thorough evaluations.
2. Budget vs Scope: Make sure the chosen provider offers value without compromising attack depth or duration.
3. Industry relevance: The requirements of a bank vary from those of a SaaS platform or a manufacturing company.
4. Reporting quality: Search for reporting that is business-friendly, straightforward, and practical.
5. Post-engagement support: The correct partner supports follow-up validation, blue team enablement, and remediation.
Choose the Right Security Approach for Your Business. Talk to our experts to find out whether Red, Blue, or Purple Teaming best fits your security needs.
Common Mistakes to Avoid When Choosing a Red Teaming Companies
Below are the common mistakes to avoid when choosing red teaming companies:
- Decision-making without reference to pricing.
- Recruiting consultants who have no offensive experience.
- Ignoring cloud-based and identity-based attack vectors.
- Selecting a provider that lacks social engineering ability.
- Penetration testing services are commonly perceived to be a red team.
- No search for certification or techniques.
Why Qualysec Is a Trusted Red Teaming Partner in Singapore
Providing high fidelity and intelligence-driven red teaming that is appropriate in the Singapore regulatory environment is a differentiator at Qualysec. They approach displays ruthless pathways of attack through human innovation coupled with advanced automation.
Customers in Singapore choose Qualysec for the following reasons:
- Knowledge in multi-cloud and hybrid-cloud exploitation.
- Advanced Artificial Intelligence reconnaissance.
- Complete simulation of the opponent (social, digital, physical)
- MAS TRM and PDPA MAS ready to be audited.
- Rapid, systematic remedial guidance.
- Sound client confidentiality and outcome accuracy.
Qualysec offers one of the strongest red teaming programs in the region to organisations interested in engaging a low-cost yet powerful offensive security provider.
Schedule your strategic Red Team consultation with Qualysec experts today!
Conclusion
Red teaming is essential to Singaporean businesses that face the threat of attack vectors related to cloud, network, and employees. Selecting an appropriate partner ensures that you discover hidden threats before the hackers, and it may be either a controlled business or a tech company that is in a fast growth mode.
Red team IT security providers, the best of which is illustrated here, have varying strengths, yet the one that will best suit your environment, risk tolerance, and compliance requirements. Leading red teaming companies like Qualysec provide a well-rounded, result-oriented Defence Validation strategy with deep offensive expertise and Singapore experience.
Check out Qualysec’s full analysis report to find your ideal Singapore Red Teaming Partner.
Speak directly with Qualysec’s certified professionals to identify vulnerabilities before attackers do.
FAQ
1. What is red teaming in business?
Red teaming is a simulated cyberattack used by ethical hackers in evaluating the security and employee awareness of a company, its detection capability, and disaster recovery preparedness. It provides a practical overview of the way hackers may gain access to systems.
2. What is an example of red teaming?
As part of realistic hacker actions, a red team can replicate a phishing attack to steal employee credentials, log into the cloud with the stolen credentials, use a misconfigured IAM role, escalate permissions, and steal sensitive data.
3. Can red-teaming now include AI / LLM safety testing, not just classic infrastructure or network attacks?
Yes. Modern red teaming is essential to businesses that rely on advanced automation because it includes AI/LLM prompt injection testing, model manipulation, attempts to poison data, jailbreak attacks, and testing of AI-driven workflows.
4. How does red-teaming in cloud / hybrid-cloud environments differ now?
Cloud Red teaming examines misconfigurations of identities, overly generous permissions, insecure APIs, serverless vulnerabilities, multi-cloud identity federation, and lateral mobility through cloud-native services. These attack routes are rather different compared to those in-premise networks.
5. Can red-teaming results help with regulatory compliance audits?
Yes. There are numerous findings to support MAS TRM, PDPA, PCI-DSS, ISO 27001, and SOC 2 compliance programs.


































































































































































































































































































































































































































































































































0 Comments