In the fast-changing world of digital business today, threats from cybercrime continue to outpace advances in technology. Business leaders know there is an importance on robust security, but throwing more tools at a problem is not always the best solution. In fact, 88% of organisations in 2025 were still having security incidents, despite having spent even more on tools. The answer is really in the process, knowing what is most valuable in your business(es), the real potential threats and how to defend them. That’s the purpose of an IT Security Risk Assessment—to provide a pathway that allows you to concentrate on what matters, set priorities, and implement stronger defences.
What Is an IT Security Risk Assessment?
An IT Security Risk Assessment is a structured view of the digital world of your business (its computers, software, networks, and data). The purpose is to determine what is at risk, how it will be attacked and how you will defend against that attack.
Once the attacks have been identified, you then rank them for likelihood of occurrence and impact should the attack happen. This framework allows you to make better decisions around risk and address the larger gaps in risk exposure, rather than trying to fix everything at once and risk missing critical areas.
Read also: How to Conduct a Cybersecurity Risk Assessment
Why Is It Important To Perform Security Risk Assessments?
Risk assessment takes you through complexity to clarity—it is vital in an era of identity-based attacks, agentic AI-based threats, and credential theft; credential theft rose 160% in 2025, now associated with 20% of breaches. Additionally, regular assessments keep you compliant with regulations such as the EU’s DORA for finance, allowing you to have the visibility you so desperately need.
Step-By-Step Guide to Conducting an IT Security Risk Assessment
An effective IT risk assessment takes a procedural approach to assist businesses in identifying risks and shoring up defences. It begins with scoping the problem and setting the scope and target, then identifying critical assets that require protection.
Once risks are defined, organisations can begin identifying potential liabilities and vulnerabilities. Risks can be categorised and ranked according to the likelihood of occurrence and probable loss amount. Once priorities have been established, security controls are implemented, and a process of ongoing monitoring is established to ensure systems remain strong against expanding and ever-changing threats.
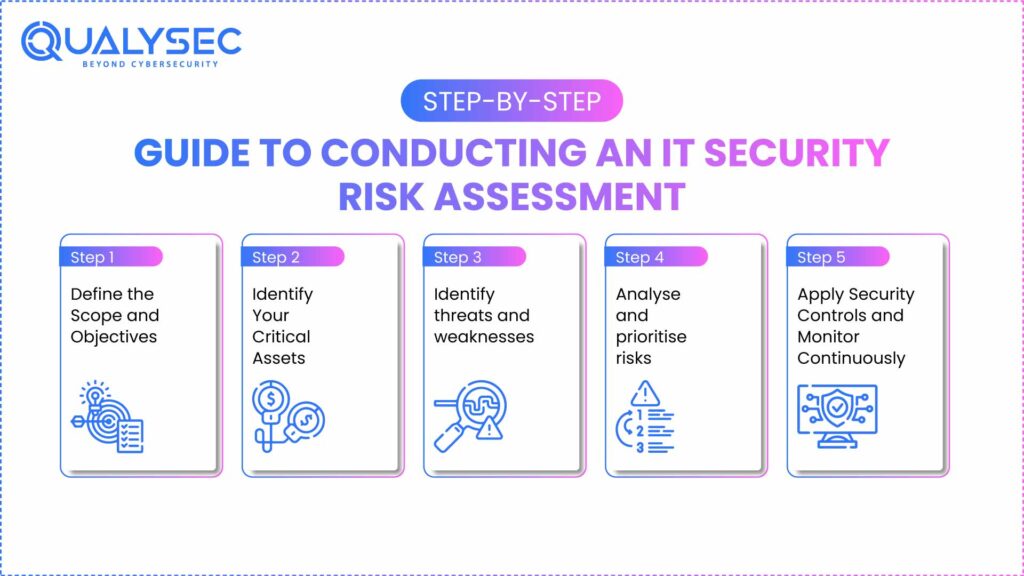
Step 1: Define the Scope and Objectives
The first step in identifying IT security risks is to establish lines of demarcation. Organisations need to establish whether the analysis will be at the organisation-level or at the area-level, i.e., cloud applications security, database security, or network-level security.
Establishing lines of demarcation will clarify where organisations need to focus their time and energy. It is also important to establish the objectives of the information security risk assessment; i.e. is the sole purpose to achieve compliance, reduce vulnerabilities, or increase capabilities overall in resilience. A well-laid-out plan at the kick-off stage will align all members and provide direction.
Step 2: Identify Your Critical Assets
The next step is to identify your critical assets. This includes customer data that is sensitive, email and internal communication systems, cloud services, physical servers, or even IoT devices.
It is important to consider criticality for business operations, as well as what attackers perceive as being the most valuable, considering your entire environment. Documenting asset information helps you know what you should be protecting. You need to know if things are at stake before creating the pertinent controls.
Protect your business before any attacks – Schedule an IT cybersecurity risk assessment today!
Step 3: Identify threats and weaknesses
Once you have your assets documented, identify the threats and weaknesses that attach to your assets. Threats that make up the first part may include phishing email attacks, ransomware, insider misuse threats, and others using new AI tools. Weaknesses include holes that you may be identifying in your defence, such as unpatched software, weak passwords, and misconfigured firewall settings.
Your threats and weaknesses can often be identified using things such as vulnerability scanners, penetration tests, and security audits. When you have your threats and weaknesses documented, it gives you the best chance possible to understand how an attack could happen.
Step 4: Analyse and prioritise risks
Not all risks are equal. This step is focused on analysing the possibility of an attack occurring and the damage the attack could do to the Agency. Many organisations will categorise risks using a risk matrix and group high, medium, and low risks.
A ransomware attack on financial systems may rank high, whereas a minor phishing attack on a test account may only rank low. The purpose of the prioritisation step is to make sure your resources and budget are first allocated to the biggest threats.
You might like to read about What is an Information Security Risk Assessment?
Step 5: Apply Security Controls and Monitor Continuously
After identifying the risks, the next step is to implement the right safety measures to reduce those risks. This could include implementing stronger passwords, encrypting data, providing employee training, regularly updating software, or monitoring programs.
What’s important is to match the action you took to reduce the risk with the specific risk that was identified above. IT security risk assessment process is not a singular process. Risks are always changing, so change, monitoring, and providing updates that ensure safety will continue over time.
Best Practices for a Successful Risk Assessment
Engage your leadership with your stakeholders. Security has become a board-level priority—not simply an issue of IT. Establish a set of assessments with a mix of automation and human expertise, frameworks like NIST, ISO 27005, or frameworks that support zero-trust and real-time visibility.
Consider assessments similar to a rhythmic movement; it’s not a one-off. Also, keep nist it risk assessments lean. Tool overload is a growing concern for 2025. Simplify, rationalise with utility, reduce confusion.
Don’t wait for a breach— Request a Qualysec Risk Assessment and download a sample pentesting report today.
Latest Penetration Testing Report

How Can Qualysec Help?
Qualysec makes it hard to manage cyber risks in an easier and effective way. Qualysec give businesses the tools to understand where their business matters most, the weak points and how to protect them. They design their foresight and approach to facilitate clear guidance, as opposed to commoditising a service for a team with complex tools and complex language. They simplify the message with clear communication.
An expert team monitors continuously and review regularly so that businesses are always aware of new threats and vulnerabilities. They have valid, easy-to-read cybersecurity risk assessment reports that clearly report what the risk is and the steps taken to manage and mitigate the risks. When they match industry standards and compliance obligations, they enable companies to build trust and confidence with customers and stakeholders.
In essence, Qualysec are not just enabling organisations to observe risk exposures but also offering to manage risk with security for today and in the future. Overall, we guarantee that you will conclude with a business opportunity to become pro cyber aware and manage vulnerabilities to excel in the future.
Protect your business from evolving threats—partner with Qualysec today.
Conclusion
An IT security risk assessment provides organisations with a clear and detailed view of their risks and how they should treat them. Organisations can make informed decisions about how to secure the most important assets and keep the security assessments evergreen. Organisations can focus on the most pertinent areas, reduce total costs, and remain prepared for future security threats.
Turn vulnerabilities into strengths with Qualysec’s expert security testing. Contact us today.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
FAQ’s
1. What Is Risk Assessment in IT Security?
Risk Assessment in Information Technology Security is the identification of the organization’s digital assets, including how critical they are to the organization. The identification of potential vulnerabilities for each asset and how they could be attacked. To develop an action plan to reduce exposure to cyber risks with appropriate countermeasures or safeguards, and to protect data, systems and operations, from potential attacks.
2. What Are the 5 Steps of Security Risk Assessment?
The five steps of a risk assessment include:
- Define the scope of the assessment and objectives;
- Identify critical assets;
- Identify potential threats to, and vulnerabilities of, each asset;
- Analyze and prioritize risks; and
- Implement current security controls or safeguards with regular monitoring.
The process of following all five steps provides an organised and standardised approach to risk assessment.
3. How Do You Conduct an IT Risk Assessment?
You will want to start your IT risk assessment by taking inventory of the key assets you want to protect. Once you’re clear on your key digital assets, identify potential threats and vulnerabilities, and then evaluate their likelihood and impact.
Once you determine this, you can prioritise risks and implement the appropriate controls to mitigate that risk. An IT security threat assessment shouldn’t be a one-off task. It should be reviewed regularly to make sure it’s relevant and effective.
4. What Are the five Things a Risk Assessment Should Include?
A cybersecurity risk assessment services providing a complete picture of your security posture should include the following five elements:
- The scope and purpose of the assessment;
- Asset inventory of critical assets;
- Threats and vulnerabilities;
- Risks with analysis and prioritization;
- Recommended security controls or safeguards and action plans.
Have any questions? Feel free to ask now—our cybersecurity experts are here to help.














































































































































































































































































































































































































































































































0 Comments