Automated threat response has evolved from a luxury to a necessity in the current environment. Today, threats are evolving quickly, which has made them a big concern for businesses. When you come across an increasing number of cyberattacks, their intensity and how complex they are, it’s quite evident to note that it is impossible to deal with them manually.
Automated Threat Detection and Response Solutions that provide continuous protection to businesses through:
- Machine Learning (ML) capabilities
- 24/7 real-time monitoring
- Deep analysis
- Managing all endpoints, networks, and cloud infrastructure
- Automated response capabilities
This allows businesses to respond in real-time to incidents that would otherwise go undetected using traditional signature-based tools.
These types of Automated threat detection and response Solutions result in organisations having the ability to quickly respond to incidents that are detected. Therefore, it limits the damage caused by an attack and increases the ability of the company to recover from the event.
Because of the growth of attacks powered by Artificial Intelligence (AI), Automated Defence has become one of the key elements in any comprehensive Modern Cybersecurity Strategy.
Why Automation Is Critical for Modern Cybersecurity
As we move into 2025, the cybersecurity threats will not only come from humans but also from automated scanning, Artificial Intelligence bot attacks, large-scale vulnerability probing and other AI applications to cybersecurity.
Automated systems will assist stressed cybersecurity teams by quickly triaging and alerting on evolving threats while also reducing the risk of human error when responding. Many organisations refer to it as a “business need”, and 97% of those that are reporting say they need to have automation as a requirement.
The automated systems that are available also provide scalability. These systems can manage multiple sources of logs, telemetry and alerts, while performing each function on its own.
This way, cybersecurity teams can have a better understanding and response to threats. They can also manage complex and growing infrastructures more proficiently.
Read more about Automated Cybersecurity Solutions for Modern Businesses
What Is Automated Threat Response? How It Works
When a security incident occurs, Automated Threat Response is the process whereby a system automatically triggers a remediation process based on predefined rules or adaptive behaviour, requiring little or no human intervention.
Detection mechanisms integrate with response mechanisms; for example, if an endpoint is compromised, the response may include isolating the compromised endpoint, blocking any suspicious traffic on the network, or quarantining a file that has been identified as malicious.
These systems use available information, including threat intelligence feeds, behaviour analysis and orchestration frameworks, to determine whether any alert requires immediate investigation and/or additional action. Once a potential security issue (i.e. a network intrusion or an attempted phishing) identifies, automated response mechanisms will perform any required tasks and report these tasks through logging.
Most of the modern cybersecurity solutions for detecting and responding to threats are being incorporated into a single solution called Automated Threat Detection and Response (ATDR), which is designed to provide real-time protection across multiple platforms and environments.
Download a sample Penetration testing report to see how automated threat response strengthens security.
Download a Sample Pen Testing Report

Core Technologies Behind Automated Detection & Response
Automated detection and response combine elements of AI, ML and Orchestration for Network Services. AI and ML enable the detection of anomalies by establishing norms for user behaviour, endpoints, and network traffic and then flagging any changes from these norms that indicate there could potentially be a threat.
Cloud and Hybrid Environments provide the ability to create a model that classifies network traffic and allows for the detection of malware using ML-based techniques, including Random Forest or Deep Learning, as documented in recent studies. Learn more about Hybrid Cloud Security Solutions.
An agent can use a response Framework (e.g., MAPE-K loops) to provide an orchestrated architecture that offers a platform for monitoring, analysis, planning, and executing actions automatically, and to provide an autonomous scale for policy-compliance-based mitigating actions across a larger infrastructure.
Furthermore, Orchestration and Automation tools connect and coordinate the above-referenced responses between Endpoints, Network Devices and Cloud Services, providing a point of consistency and repeatability to reduce the occurrence of human error and allow for what some have deemed “Self-Healing” Security.
You might like to know more about the Cybersecurity Risk Assessment Frameworks for Businesses Guide.
Automated Response Workflow: From Alert to Containment
Automated response workflows typically begin when a detection component perceives abnormal behaviour through a sudden increase in failed login attempts, unidentified network activity, or recipients receiving phishing attempts via e-mail, etc. Next, analysts complete a security assessment of the context of these events to determine user/user information and asset importance compared to normal historical trends, along with known threats based on previous intelligence.
If conditions are met, such as predefined thresholds or AI-produced confidence levels, the system performs predetermined actions. It isolates affected endpoints, blocks or limits network traffic, quarantines suspicious email or files, and disables accounts that may be compromised.
Each action taker will log. Many frameworks send alerts to human analysts so they can either continue to investigate or assist with the investigation of another component of the workflow.
The final part of each workflow consists of gathering all the necessary forensics and can also eventually lead to the “fix” stage (e.g., applying a patch, reconfiguring). This also serves as an opportunity for the automation of these steps to allow for quick remediation with a minimal amount of work from an individual processor/ human analyst.
Read also: Third Party Risk Management: 2026 Complete Framework
Key Benefits of Automated Threat Detection & Response
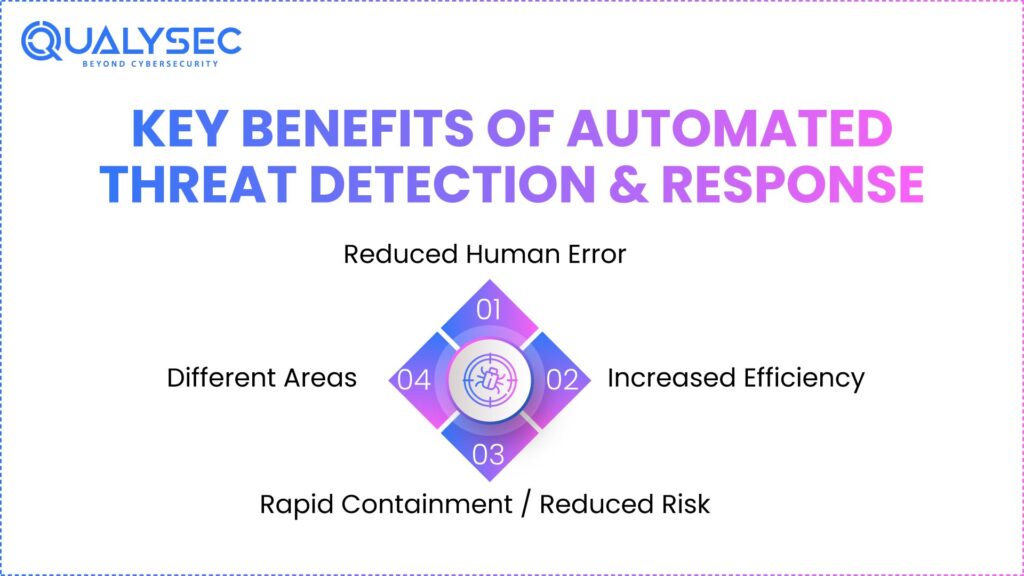
Automated threat response and detection are important parts of a strategy to protect against cyber threats. Real-time detection and response are possible these days. Cyber threat detection can immediately identify network security threats like phishing scams or network intrusion attempts. There are some other benefits as well, like:
Reduced human error: Automated processes follow established procedures for threat mitigation. This process allows organisations to deliver predictable and consistent results in response to threats and reduces the chance of human error due to stress and pressure.
Increased efficiency: Many cybersecurity professionals will no longer need human intervention for many repetitive and time-consuming functions, and software will automatically complete them, which will allow security teams to focus on more strategic initiatives and objectives.
Different areas: Different sources, including endpoints, networks, cloud-based systems, and endpoint protection solutions, use automated systems to manage events and data. This makes them especially effective for architectures that have complexity or are hybrid.
Rapid Containment / Reduced Risk: Speedy automated actions, such as responding to Network Intrusion (NIR), facilitate a faster containment of incidents and significantly reduce the risk of harm to the business through a shorter time frame of being vulnerable.
Want deeper insight? Contact Qualysec to know the full potential of automated threat detection & response.
Get Your Free Security Assessment
How Automation Reduces Breach Impact and Response Time
Integrating automated threat detection and response into an organisation, supported by automated security tools, results in a substantial decrease in the consequences of a breach as well as the amount of time necessary to respond to it.
Automatic Threat Detection and Response System – can take milliseconds or seconds to detect and respond to a threat (compared to hours and days for manual processes).
Rapid isolation of infected Systems and Accounts effectively stops the movement of the attack, so that they cannot make it to protected data or critical systems.
Automated systems reduce False positives and prioritise security Threats correctly, enabling security teams to focus their resources on only the real threats, which ultimately saves time and reduces the potential for alert fatigue. As a result, organisations can reduce their operational and financial risks associated with a breach while recovering more rapidly with minimal downtime.
Role of Automated Threat Response in Endpoint, Network & Cloud Security

Automation of Threat Response Is Critical to Modern Security in Multiple Layers of Infrastructure:
- Endpoint Security: Automated phishing response and endpoint behaviour monitoring allow for the rapid isolation or quarantine of compromised devices or accounts. Learn more about Endpoint Security Service.
- Network Security: In the case of network intrusions, security systems enact automated responses to suspicious traffic immediately to block or contain the attack so it cannot spread laterally.
- Cloud and Hybrid Security: Automated processes used to detect anomalies in traffic, user actions and API calls in the Cloud and Hybrid Environments, provide automatic methods of containment, such as disabled access and quarantine, thus maintaining compliance and minimising the risk of a breach.
Talk to our experts to see how AI-driven network security can help you detect, prevent, and respond to attacks faster.
Challenges of Automated Security Systems
Automation can create value, but there are also many potential disadvantages associated with it. Complexity of Integration: Integrating automated detection systems into existing IT infrastructures and hybrid environments with differing technologies can present many challenges.
Training Quality and Data Sets: Many AI/ML systems depend heavily upon high-quality databases. Thus, when there is a significant amount of low-quality and/or inconsistent training data within those databases, this can lead to an elevated level of false positives, inaccurate detections and/or undetected or insufficiently addressed threats.
False Positives / Alert Fatigue: Poorly set thresholds or improper tuning associated with automated detection systems can lead to the generation of excessive alerts and negatively impact the efficiency and effectiveness of these systems.
Concerns about Policy and Control: A fully automated response to detected threats poses the potential for unintended consequences. Therefore, many organisations employ human oversight, AI security measures, and/or strict rules of engagement to reduce this risk.
Skill Level Requirements: As automated detection systems and technologies become increasingly sophisticated, the skill sets required for the operation and maintenance of these systems will require individuals with very specific training (security architects and data scientists). Thus, there may be difficulties locating and retaining these types of individuals.
Connect with Qualysec to discover how ML-driven cybersecurity can secure your endpoints, networks, and cloud.
Best Practices for Implementing Automated Detection & Response

Organisational adoption of Automated Threat Detection and Response maximises effectiveness, while minimising risks by:
Taking a phased-funnel approach, beginning with monitoring and alerting utilising the automated system and advancing gradually to automated containment once there is a comparatively high level of confidence and satisfactory tuning.
Utilising high-quality and diverse training datasets, ensuring that both datasets are trained on real-world operations and normal user activity, and have various types of cyberattacks classified within the dataset, thereby increasing detection accuracy.
Defining and establishing clear guidelines and rules for engagement—deciding which responses the automated system can handle, which will need human approval, and which are off-limits to avoid unintentional service disruption, including AI image generation tools.
Ongoing Monitoring and tuning- continually review false positives, unsuccessful detection events, and the behaviour of the automated system, whilst also continuously reviewing and refining thresholds, models and other workflows.
Integrating threat intelligence continuously- keeping up-to-date with current threat signatures, threat patterns and IoCs, and continually updating the automated threat detection process to be able to defend against continuously evolving attacks.
Read also: Cybersecurity Best Practices: How to Protect Your Business.
Find Your Perfect Security Partner
Why Automated Tools Still Need Expert Penetration Testing
Although automated systems are sophisticated, they cannot replace the creativity, intuition, and strategic insight of human security professionals. Therefore, network security testing performed by human security professionals is necessary for many reasons:
As new attack vectors develop that are not typically part of automated detection processes, only human security professionals would recognise and validate these attack vectors or exploit the logic of vulnerabilities in these new attacks.
Network penetration tests also provide a means to test the efficiency of automated detection and response processes under “normal” conditions, making certain that automated detection processes work in a production environment.
Human penetration test professionals can simulate realistic, complex multi-stage attacks by combining various attack vectors (e.g., combining social engineering with lateral movement and privilege escalation). They can create attacks that would typically avoid detection from automated systems.
Network penetration testing provides opportunities to discover misconfigured or incorrectly configured devices or systems and to identify edge cases that may not have been detected by automated systems, therefore closing the gaps in a business’s security processes.
Reach out to our experts to understand how advanced penetration testing services uncover critical vulnerabilities before attackers do.
Conclusion
With the increase in complexity in the Cybersecurity ecosystem and the increase in the usage of AI and Automation by cyber adversaries, organisations need to develop an Automated Threat Response Strategy.
An Automated Detection System that incorporates Response Orchestration provides Real-Time, Scalable, and consistent protection. It allows organisations to quickly view and contain Phishing, Intrusions, and Other forms of Automated Threats response before any damage takes place.
Organisations still face many challenges when it comes to Integration, Data Quality, and Human Error, but if they follow certain best practices and conduct manual penetration testing consistently, they can provide a Strong, Balanced Security Posture.
Through this process, organisations no longer have to operate with a reactive defence. Instead, they can adopt a resilient self-healing defence model and protect endpoints, networks, and cloud assets from cyber threats of the 21st century.
Schedule a meeting with our experts to understand how automated threat response & detection can secure your business.
Speak directly with Qualysec’s certified professionals to identify vulnerabilities before attackers do.
FAQ’s
1. What is automated threat response, and how does it work?
Automated Threat Response (ATR) is the process by which systems identify, evaluate and react to threats without needing human involvement or decision-making. ATR takes advantage of either pre-determined rules or artificial intelligence (AI) to automatically identify and eliminate Threats as soon as they detect them.
2. How fast can AI respond to security incidents?
The AI technology used for Incident Response can identify and respond to a Security Incident within seconds or milliseconds. This rapid response capability ensures that a potential Threat, such as malware, phishing, or unauthorised access, will be contained before it can cause serious harm.
3. What types of threats can be automatically remediated?
Automated systems can remediate Threats such as phishing attempts, malware, suspicious logins, DDoS attacks and misconfigured access permissions. Typically, they prioritise low-risk incidents for automatic remediation.
4. What are the benefits of automated responses to reduce security team burnout?
Automated response systems help reduce the amount of manual labour associated with responding to repetitive or high-volume alerts. By automating many of these tasks, security analysts can devote their time and energy to more difficult investigations. The result of decreased manual labour by team members is a reduced chance of experiencing burnout and an improvement in the overall productivity of these teams.
5. What is the major difference between a SIEM and SOAR?
SIEMs (security information and event management) provide a central location where an organisation can collect security data and correlate it for monitoring and generating alerts; whereas SOARs (security orchestration, automation, and response) provide automated responses to alerts generated by SIEMs. Essentially, SIEM identifies issues, while SOAR takes action on those issues.
6. What is an automated response system?
An Automated Response System is a type of security solution that can detect potential threats and carry out pre-configured responses (e.g., blocking an IP address, isolating an endpoint, or sending out team notifications). This allows organisations to minimise or eliminate damage from a security incident while simultaneously not requiring human involvement to take action.
7. What is automated threat detection?
Automated threat detection combines the use of artificial intelligence, machine learning, and rules-based systems to allow continuous monitoring of suspicious activity. It also helps identify abnormal activity, potential attacks, and vulnerabilities in real-time, enabling organisations to react faster to threats.














































































































































































































































































































































































































































































































0 Comments