Cyber threats are developing faster than existing security solutions. Organizations nowadays have to deal with smart, adaptive, and difficult-to-detect threats ranging from automated phishing scams and unheard-of data breaches to AI-powered cyber attacks. Cybersecurity teams also need to improve their approach as attackers embrace automation and machine learning. AI for Cyber Attack Prevention, combined with human expertise, can prove useful.
Modern security paradigms go beyond detection and reaction. Instead, firms are moving toward Proactive Threat Prevention, whereby artificial intelligence forecasts and stops attacks before they cause any damage. This makes artificial intelligence a fundamental support in preventing AI cyber threats, stopping AI attacks, and lowering the hazards posed by AI hacking methods.
Why Cyber Attack Prevention Needs AI
Hackers are increasingly using automation, deep learning, and large-scale data processing to launch complex and adaptive attacks. According to cybersecurity research:
- Creation of automated malware
- AI-created phishing
- Clever brute force attacks
- Adaptive self-learning cyberattacks
AI for Cyber Attack Prevention is essential because:
- It examines huge datasets in real-time.
- It identifies attack patterns people miss.
- Using AI Risk Assessment, it forecasts vulnerabilities.
- It automatically arranges preventative action without requiring alerts.
Before hackers discover hidden threats, Qualysec employs sophisticated artificial intelligence models to find them. Contact us to find out how predictive testing can safeguard your infrastructure.
How AI Predicts and Identifies Threats in Advance
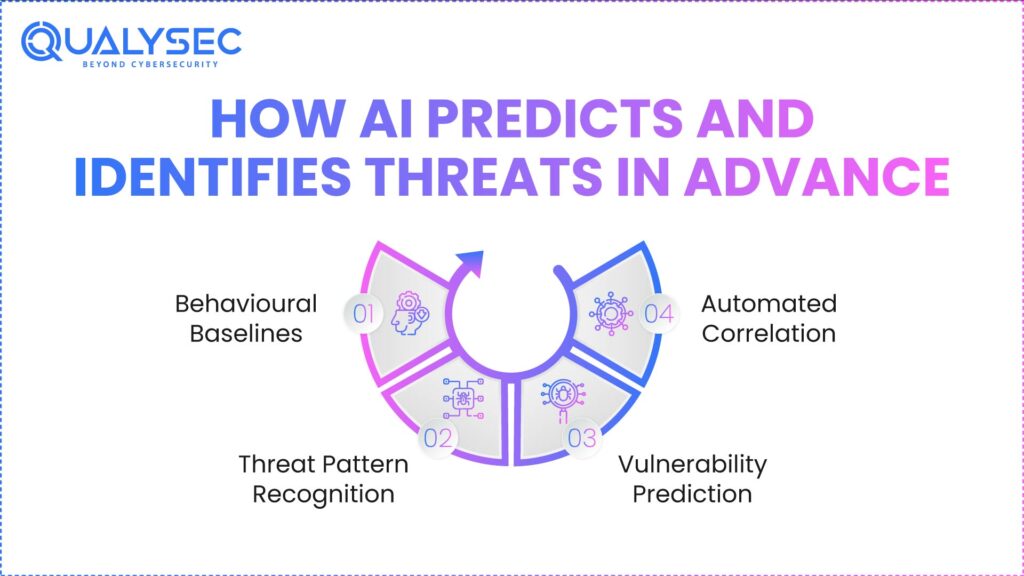
Artificial intelligence passes beyond signature-based identification. It identifies hostile activity before it grows using behavioural analytics, anomaly detection, and machine learning algorithms. This makes AI for Cyber Attack Prevention highly effective in early prediction, especially when combined with advanced machine learning cybersecurity techniques, especially when combined with advanced machine learning cybersecurity techniques.
The AI-driven predictive defense includes:
1. Behavioural Baselines
AI learns what “normal” looks like with applications, endpoints, and your network. Any variation starts an inquiry.
2. Threat Pattern Recognition
Using millions of known cyber incidents, artificial intelligence enhances AI threat detection by spotting attack signatures early, long before they develop into large-scale invasions.
3. Vulnerability Prediction
Using Vulnerability Prediction algorithms, artificial intelligence can project which systems are most likely to be attacked next.
4. Automated Correlation
AI links user behaviour, traffic data, logs, and threat feeds to uncover hidden hazards otherwise unnoticeable manually. This capacity to foresee risk turns artificial intelligence into a strong tool against artificial cybersecurity risks.
Read also How to Conduct a Cybersecurity Risk Assessment?
AI-Powered Threat Intelligence & Early Warning Systems
Predictive threat intelligence, in which artificial intelligence constantly searches the digital ecosystem for new indicators of compromise, is a cornerstone of modern cyber protection and supports powerful automated cybersecurity solutions.
Artificial intelligence improves threat awareness by means of:
- Automated threat feeds analysis
- Cross-network aberration detection
- Real-time worldwide threat detection
- Indicators of compromise based on artificial intelligence
- Forecasting attacker behaviour using predictive models
This transforms unprocessed data into useful insights that enable businesses to avoid attacks before they occur.
With Qualysec’s AI-based security system and threat intelligence, improve your early-warning skills. Let us help you outrun hackers.
Speak directly with Qualysec’s certified professionals to identify vulnerabilities before attackers do.
Preventive Security Automation: Blocking Attacks in Real Time
Real-time automated prevention is a core benefit of AI for Cyber Attack Prevention. This includes:
1. Instant Traffic Blocking
Using predictive analysis, AI firewalls instantaneously blacklist dangerous IPs, domains, and ports. They also continuously adapt block lists based on emerging threat intelligence to stop attacks before they escalate.
2. Automated Incident Response
AI stops lateral mobility, suspends harmful processes, and separates compromised devices. This also triggers automated playbooks and restores them with minimal human input.
3. Email Security Automation
Artificial intelligence filters phishing attempts, spoofed domains, and harmful attachments. Furthermore, it examines message intent and sender reputation to stop even zero-day social engineering efforts.
4. AI-Based Endpoint Protection
Real-time monitoring of advanced endpoint solutions scripts, memory behaviour, and suspicious commands. Automation lowers breach time from hours to seconds. Furthermore, guaranteeing complete endpoint recovery, it also promotes automated correction actions, including rollback, isolation, and file quarantine.
You might like to know about Automated Threat Response & Detection.
Using AI to Strengthen Vulnerability Management
Periodic scanning is the foundation of conventional vulnerability assessment. Using artificial intelligence prediction algorithms, this becomes proactive, continuous security thanks to artificial intelligence.
Artificial intelligence helps by:
- Giving vulnerabilities priority depending on the exploit possibility.
- Studying attempted exploits all around the world.
- Foreseeing the next attack points for the hackers.
- Continuous monitoring rather than point-in-time scanning will help.
Organizations get a strong edge by resolving their most important vulnerabilities with Risk Assessment AI.
Learn more about Vulnerability Management Services – An Ultimate Guide
AI in Proactive Penetration Testing
AI is instrumental in next-generation penetration testing by:
- Automated reconnaissance
- Smart use of simulation
- Behavioural assault mapping
- Predictive risk assessment
- Machine learning–powered test case creation
While security analysts confirm and validate results at Qualysec, the artificial intelligence system finds hidden flaws using behavioural analysis and pattern detection. This combined approach offers the best precision and comprehensive risk coverage.
Qualysec’s artificial intelligence penetration testing finds secret attack routes and imitates actual hacker behaviour. Create a customized testing plan today.
Stopping Zero-Day Attacks with Predictive Models
Zero-day vulnerabilities are hazardous since there is neither a signature nor a patch. AI helps to prevent zero-day attacks by:
- Investigating erratic code execution
- Anticipation of harmful patterns in fresh files
- Assessing network traffic behavioral shifts
- Employing threat models based on worldwide attack statistics
Within seconds of starting, AI-powered behavioral detection can stop zero-day attacks—even without any prior awareness of the threat.
Early zero-day defense needed? To ensure your systems are ahead of new risks, Qualysec uses predictive analytics and artificial intelligence-based modelling. Read our case studies.
See How We Helped Businesses Stay Secure

Challenges in AI-Driven Cyber Prevention
Though it is powerful, artificial intelligence meets challenges:
- False positives resulting from excessively sensitive models
- Adversarial attacks in which hackers deceive artificial intelligence (AI) systems
- Model drift is where previous patterns turn obsolete.
- Dependency on data quality
- Initial implementation expenses are great.
Though strong, artificial intelligence is not flawless; it calls for experience, observation, and ongoing optimisation.
Human Oversight: Why AI Alone Isn’t Enough
Every alert is validated by competent analysts for optimum precision and minimum false positives in Qualysec‘s hybrid artificial intelligence, along with a human security model.
Although people still matter, artificial intelligence speeds cybersecurity. Humans offer:
- Contextual comprehension
- Ethical assessment
- Adaptive Innovation
- Verification of ambiguous threats
- Decisions driven by strategy
While humans offer the vital decision layers, artificial intelligence manages speed and scale.
Together, they construct a balanced next-gen cybersecurity with AI.
How Qualysec Helps Build an AI-Ready Cyber Defence Strategy
Qualysec incorporates artificial intelligence cybersecurity into companies through:
1. AI-Assisted Penetration Testing
Uses predictive algorithms to expose the most extreme vulnerabilities. Furthermore, utilizing artificial intelligence-driven exploit paths, it simulates hacker behavior to expose flaws that conventional testing could overlook.
2. Continuous AI Monitoring
Real-time defense against changing threats. Moreover, it links millions of event logs to find anomalies that point to undetected or developing cybersecurity threats.
3. Predictive Threat Intelligence Systems
Early detection of growing assault patterns. These systems forecast hacker strategies before they get to your surroundings using behavioral analysis and global threat feeds.
4. Automated Vulnerability Management
Make certain priority repairs keep ahead of hackers. Automation scan also suggests remediation measures and confirms patch success to make sure no vulnerable flaws persist.
5. Building AI-Ready Cyber Policies & Architecture
Making your defence approach future-proof. Furthermore, creating long-term resilience and flexibility, Qualysec develops scalable systems that fit naturally with developing artificial intelligence security tools.
The hybrid human plus artificial intelligence model of Qualysec provides companies with the greatest degree of proactive cyber protection.
Download the full AI Security whitepaper for deeper insights.
Conclusion
Cybersecurity now depends on artificial intelligence, so AI for Cyber Attack Prevention has become essential in modern cybersecurity. It forms the foundation of modern proactive threat prevention. Organizations must match sophisticated defensive systems as hackers deploy AI cybersecurity threats using machine learning, automation, and AI-driven methods.
AI guarantees threats are stopped before they happen, from AI security vulnerabilities to real-time prevention, predictive modelling, and automated incident response. Combining professional human monitoring with professional guidance from companies such as Qualysec helps businesses construct a defense against rapidly changing cyber threats.
Discover how businesses benefit from predictive, proactive, and automated protection. Read our client testimonials and connect with Qualysec today.
See Why Companies Worldwide Trust Us

FAQs
1. How does AI prevent cyberattacks proactively?
AI finds risk before execution and automatically stops harmful activity using behavioural analysis, threat prediction algorithms, and anomaly detection.
2. Can AI identify attack patterns before they occur?
Yeah. Millions of threat signals are examined by artificial intelligence, which also relates patterns across the world and projects future attack strategies by hackers.
3. What is predictive threat intelligence?
By examining behaviours, worldwide threat data, and new vulnerabilities, predictive threat intelligence uses artificial intelligence and machine learning to forecast future attacks.
4. How effective is AI at preventing phishing attacks?
By looking at language patterns, sender behaviour, and harmful link signatures, artificial intelligence identifies phishing with very good precision.
5. What percentage of attacks can AI prevent automatically?
AI can automatically stop 70 to 90 percent of typical cyberattacks, particularly malware, phishing, and brute-force tries, depending on system maturity.
6. What are the 5 advantages of AI in cybersecurity?
Five benefits of artificial intelligence in cybersecurity are as follows:
- Real-time automatic threat avoidance
- Predictive vulnerability detection
- Better, faster detection
- Fewer false positives
- Solid defence against an initial attack


































































































































































































































































































































































































































































































































0 Comments