The Indian digital economy is growing rapidly, connecting businesses, but also making them increasingly vulnerable. By 2025, cyberattacks against companies in India will have become even more sophisticated, frequent, and costly than in the past, particularly for cloud-first and mobile-first environments. Companies are scaling up their digital operations, and, therefore, it is necessary to conduct an Enterprise security assessment on the company’s current level of protection.
There are also increasing demands for compliance with regulatory requirements, an increasing number of ransomware attacks, and increasing complexity of IT ecosystems, which create the need for companies in India to have more than just a basic firewall and old-fashioned protective technology.
Companies today can do so much more to reduce their exposure to cyber risk, strengthen their company’s IT security level, and ensure the continued protection of their enterprise data by developing and implementing a strategy to monitor and enhance their security posture proactively.
The Expanding Attack Surface in Indian Businesses
Increased cyberattacks in India are a result of the rapidly changing digital landscape, which exposes numerous vulnerabilities. Increasing multi-cloud implementations, widespread acceptance of enterprise mobility security, and increased integration of third-party software as a service (SaaS) have created complexity in the ability of enterprises to protect themselves against cyberattacks.
Companies are finding it increasingly challenging to properly manage risk as they have adopted new business practices, including remote workforce environments, that have significantly impacted their cybersecurity posture and the need for regular cybersecurity assessments. With the number of devices, applications, and data growing exponentially, unless organisations upgrade their cybersecurity defence posture on a regular basis, they will continue to experience an increasing level of risk.
1. Remote workforce and hybrid work environments
As organisations transition to hybrid or remote work environments, the number of organisations relying on cloud-based collaboration tools or their employees’ unsecured home networks is growing rapidly.
Many organisations are having difficulty implementing a zero-trust approach, enforcing Multi-Factor Authentication (MFA), and continuously monitoring remote environments to ensure protection against credential theft, lateral movement, and VPN abuse. Organisations should perform enterprise vulnerability assessments routinely to remain protected against attacks that exploit these vulnerabilities.
2. The expansion of the Internet of Things and Shadow IT
Organisations are deploying the Internet of Things (IoT) at increasing rates in the manufacturing, logistics, healthcare, and retail sectors; however, the rate of security controls being added to the framework for IoT deployments has not kept pace with the expansion. As a result of the increased rate of growth of IoT deployments, there has been a corresponding increase in Shadow IT, where employees are downloading and using unapproved applications.
The proliferation of Shadow IT increases the number of endpoints on which attackers can operate and creates blind spots in an organisation’s overall IT. Consequently, the need to implement structured enterprise security solutions that enable organisations to maintain visibility over all enterprise assets is imperative.
3. Multi-cloud and SaaS Complexity
The rise of multi-cloud deployments is becoming more prevalent in India as businesses look to increase scalability and optimise costs; however, the majority of breaches are caused by misconfigured settings. Issues surrounding exposed storage buckets, weak access policies, and insecurity of third-party services lead to a phenomenon known as “security drift.” Businesses that perform periodic enterprise security assessments and cloud security testing are better positioned to identify configuration gaps and improve enterprise cybersecurity in distributed environments.
Explore our insights on Enterprise Cloud Security today.
Common Security Gaps Found in Indian Enterprises

While many Indian companies are becoming more aware of the need for enterprise security frameworks, they still have outdated practices and systems that leave them vulnerable to cyberattacks. In addition to having immature or nonexistent enterprise security processes, Indian organisations are also failing to fully invest in security automation and conduct regular Red Team exercises.
Within an organisation, the gaps in the areas of Enterprise Application Security, Configuration Hygiene, Incident Readiness & Incident Response, and Identity Governance can expose the organisation to inappropriate or unpreventable risk. Until a business resolves these risks, it opens itself to operational disruption, potential data loss, and long-term damage to its reputation.
1. Legacy systems and outdated infrastructure
Many large Indian companies continue to operate using legacy systems that are on-premise rather than hosted in the cloud and do not offer modern security capabilities. Therefore, the legacy systems are struggling to withstand new attack technologies such as Advanced Persistent Threats (APTs) and zero-day exploits (0-Days). The best way to protect the organisation from such threats is by implementing a consistent enterprise-wide risk assessment and infrastructure security assessment process to identify potential vulnerabilities before attackers can exploit them.
2. Weaknesses in Identity and Access Management
Many Indian organisations have significant weaknesses with respect to effective access governance processes. An increased number of users with excessive privileges, or shared accounts, along with insufficient user lifecycle management, can make internal security threats and/or credential-based attacks quite easy. IAM audits should be incorporated within the organisation’s enterprise security solution(s), as part of the overall enterprise security programme.
3. Lack of Monitoring and Preparedness for Security Incidents
Most organisations have no real-time threat detection capability or formal incident response plan. When an organisation experiences a security breach, it can take time for the organisation to begin containing the breach, which results in greater financial loss or operational disruption.
To be effective in the fight against emerging security threats, the organisation needs to continuously monitor for security threats, conduct periodic “dry runs” of its incident response plan(s), and participate in periodic enterprise vulnerability assessment and remediation efforts.
Explore our latest article on the top Vulnerability Assessment Companies.
Download a Sample Pen Testing Report

Why Companies In India Need Regular Enterprise Security Assessments
As cyber threats continue to rise, Indian businesses must take a proactive approach, rather than responding reactively to cyber threats. Various regulatory mandates from CERT-In, RBI, SEBI, and specific industry policy frameworks require organisations to implement stronger cybersecurity capabilities.
Conducting regular security assessments at the enterprise level will enable organisations to identify vulnerabilities, evaluate the risks associated with enterprise mobility security, and validate the effectiveness of existing enterprise security solutions. As cyberattacks become increasingly automated, artificial intelligence (AI)-driven and targeted, Indian businesses must continue to develop their defence capabilities to meet these new threat vectors.
1. Expanding Threat Complexity
Cybercriminals have begun incorporating automated malware and advanced social engineering techniques into their attacks, leveraging artificial intelligence (AI). Because organisations do not routinely conduct vulnerability assessments of all aspects of their enterprise, it is difficult to identify unknown paths to attack. Conducting detailed assessments of an organisation’s risk allows for proactive updates to existing security controls.
2. Stringent Regulatory & Compliance Requirements
The Indian environment is becoming increasingly regulated with respect to log retention and breach reporting for enterprise data protection. Therefore, a periodic review of compliance is required to ensure compliance. Periodic reviews of compliance include assessments of an organisation’s ability to support its governance and risk management responsibilities through statutory regulations.
3. Increased Supply Chain & Third-Party Risk
India’s supply chain is rapidly growing, while vendors are exhibiting poor security practices. If one vendor is compromised, that compromise may easily propagate into an organisation. Regular assessments of an organisation’s vulnerabilities against each cybersecurity risk that arises from a vendor relationship assist in remediating any supply chain security risks that may arise.
Benefits of Conducting Regular Enterprise Security Assessments
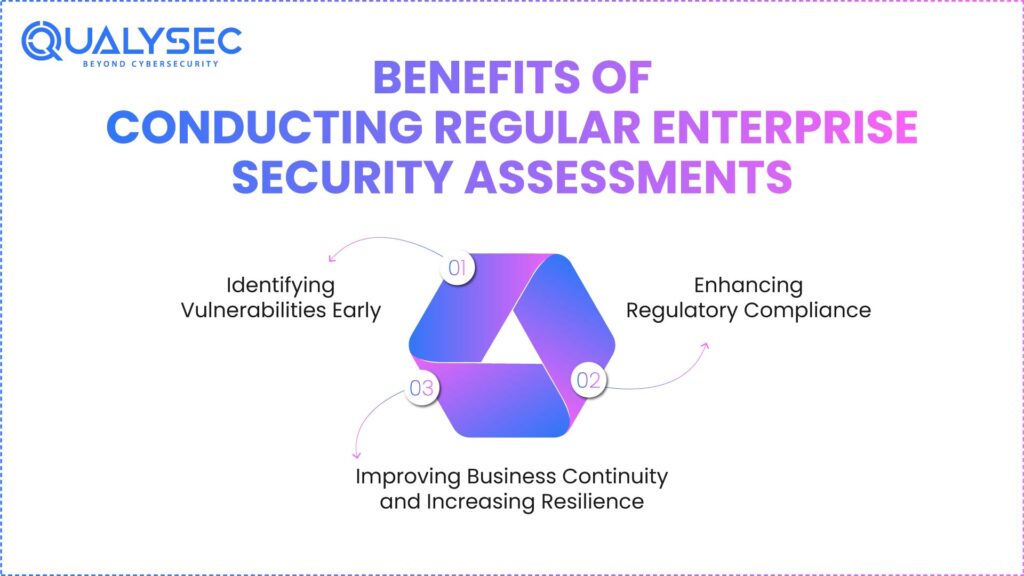
Regular enterprise security assessments will help to improve both the operational and strategic benefits of Indian organisations through the establishment of a better security posture. In addition to identifying vulnerabilities, security assessments will increase an organisation’s level of security maturity and reduce the overall cost of information security.
Security assessments will also build trust with customers due to their ability to transform an organisation’s application security, increase cyber resilience, and provide an organisation with a seamless way to safeguard data throughout an entire organisation’s architecture.
1. Identifying Vulnerabilities Early
By carrying out routine security assessments, organisations can find out about their vulnerabilities before hackers do. Consequently, by finding out first, organisations can reduce their exposure windows, thus greatly enhancing their level of cybersecurity.
2. Enhancing Regulatory Compliance
Organisations today are required to comply with more regulatory requirements than ever before, including those from the RBI, CERT-In, SEBI, IRDAI, and DPDP Act. Organisations must ensure they comply with these regulations by conducting security assessments regularly and thereby protecting against potential penalties.
Simplify SEBI cybersecurity compliance with proactive security assessments.
3. Improving Business Continuity and Increasing Resilience
Security assessments will ensure that organisations are ready to deal with the cyber threats that they face. As a result of regularly conducting security assessments, an organisation can develop robust incident response capabilities, which will allow it to be more operationally resilient and have lower costs associated with security incidents going forward.
Best Practices for Enterprise Security Assessments in India
To attain a consistent security outcome, structured assessment methodologies must be adopted by Indian companies. Best practice methodologies consist of continuous vulnerability scanning, zero-trust principles, red teaming, and alignment with international standards (i.e., NIST, ISO 27001, and CIS Benchmarks) to best strengthen enterprise mobility security, IAM, and endpoint protection and build a mature assessment lifecycle.
1. Create a Regular “Assessment Cadence.”
Companies should create an annual comprehensive assessment schedule and also implement a quarterly enterprise-wide vulnerability assessment that is tracked continuously. The quarterly vulnerability assessment allows for quick identification of new vulnerabilities, allowing for a quicker remediation cycle.
2. Integrate Assessments with Governance and Risk Management
Companies should integrate security assessments with enterprise security risk management strategies to provide a continuous flow of information from assessment results into Governance Risk & Compliance dashboards, thereby establishing measurable Key Performance Indicators (KPIs) and enhancing the efficacy of security decision-making at the enterprise level.
3. Implement Continuous Monitoring and Zero-Trust Principles
The use of continuous monitoring tools, micro-segmentation, identity-based access, and multi-factor authentication will effectively reduce the size of the attack surface. By employing these security controls, organisations are in a better position to improve the security outcomes established through their enterprise security assessments and establish a sustainable security defence framework.
Choosing the Right Security Assessment Partner in India
Indian organisations either need to establish partnerships with a certified and reputable security assessment provider in order to gain the ability to receive accurate and valid security assessment results, with specific action-based remediation plans.
As such, enterprises should partner with Security assessment Providers who have enterprise-wide Cybersecurity as well as Cloud Security, and Enterprise Application Security Expertise. The methodologies, technology stack, and certifications of the provider must all align with the organisational goals of the Enterprise.
1. Consider Expertise and Technical Capabilities
Select a Partner with a demonstrated Track Record within the BFSI, Health Care, IT/ITeS, Manufacturing, Telecom Industries, or similar sectors. In addition, the security provider must have substantive expertise with enterprise-level security Solutions such as Vulnerability Assessment and Penetration Testing (VAPT), Cloud Security, and Identity & Access Management (IAM) Audit.
2. Verify Certifications and Framework Capability
The security provider should hold certifications including CREST, ISO 27001 Lead Auditor, OSCP, CEH, and CISSP. In addition, the provider must follow Global security standards (i.e., Frameworks) when performing security assessments in order to ensure accuracy of the assessment as well as protection of Enterprise Sensitive Information.
3. Review Reporting Quality and Remediation Guidance
A quality Partner provides an enterprise with valid security assessments, well-noted action-based recommendations for remediation, risk opinion matrices, and a comprehensive remediation plan. A quality Partner’s comprehensive reporting of the results of the enterprise security assessment provides the enterprise with the ability to reliably measure improvements based on the results from the enterprise security assessment.
Check out our blog for tips and guidance on QualySec security audit services.
Speak directly with Qualysec’s certified professionals to identify vulnerabilities before attackers do.
Conclusion
There is a rapidly changing and increasing threat environment as a result of digital transformation, global intelligence networks, and sophisticated threat actors. In order to be successful and resilient, companies need a structured approach to enterprise security through regular enterprise security assessments that identify vulnerabilities, adopt a robust enterprise mobility security control system, and continuously monitor for enterprise vulnerabilities.
The combination of these three components allows Indian organisations to build strong enterprise security maturity while providing operational excellence and a digital future that generates confidence in enterprise security.
FAQ’s
1. What is an enterprise security assessment?
An enterprise security assessment consists of a methodical evaluation of the IT infrastructure of an enterprise, its cloud environments, etc. It will help you determine the lack of safety of an enterprise’s cyber-abilities.
2. Why do businesses need an enterprise security assessment?
Enterprise security assessments will allow you to find dangers to your company before an attacker can get to them. They will also provide an overall assurance of your compliance with the regulations related to the type of data a business protects. In addition, they will provide your organisation with the opportunity to make educated and informed decisions regarding funding their own security.
3. What does an enterprise security assessment include?
The security assessment typically includes everything from vulnerability assessments and penetration tests to cloud configuration audits and enterprise application security tests through IAM reviews. It includes a review of each company’s network as well as a review of their applications, endpoints, third-party vendor connections, and compliance requirements.
4. How often should enterprises conduct a security assessment?
Enterprises should perform a full security assessment once every twelve months, and quarterly vulnerability assessments as required for the organisation. For those organisations classified as high-risk or cloud-first organisations, more frequent assessments may be appropriate.
5. What are the goals of an enterprise security assessment?
The primary goal is to identify security vulnerabilities with an enterprise’s security posture and ensure that an enterprise has sufficient safeguards in place to reduce the potential for victimisation from cyber threats. Furthermore, it verifies that an enterprise has met all of its risk management and compliance obligations.
6. What can you expect to gain from enterprise security assessments?
There are many advantages, but a few key advantages of an enterprise security assessment are early detection of cyber threats, the ability to comply with regulatory standards, reduced risk of a data breach, better overall enterprise security posture, and increased preparedness for security incidents. Additionally, enterprise security assessments provide an opportunity for enterprises to optimize the effectiveness of their security solutions and overall solutions’ long-term costs.
7. Do enterprise security assessments also check for cloud security compliance?
Yes! Modern enterprise security assessments now typically include checks for cloud security compliance, such as a review of the enterprise’s cloud computing environment, identity and access audits, and assessments of vulnerabilities within enterprises’ multi-cloud and software as a service (SaaS) environments. These types of assessments have become even more important as a larger percentage of an enterprise’s workload has migrated to the cloud.


































































































































































































































































































































































































































































































































0 Comments