SOC 2 compliance certification has become one of the most reliable trust signals you can offer partners or clients in 2026. This is mainly applicable for SaaS, cloud, and service firms selling into global and U.S. markets. However, it is important to know more about SOC 2 Compliance Certification to ensure there are no mistakes made.
People often call it the “SOC 2 certification,” which is actually misleading. In reality, what you receive is a SOC 2 attestation report issued by an independent auditor, based on your control environment and operational consistency.
In this guide, we offer a step-by-step path to getting SOC 2 type 2 certification, coupled with evidence mapping, timelines, and context.
What Is SOC 2?
SOC 2 is the abbreviation of Systems and Organization Controls 2. One should also note that it is not a conventional certification. Rather, it is a statement of an independent CPA firm that tests whether you have a functioning control environment as per the Trust Services Criteria. These are Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Type 1 vs Type 2: Understanding the Difference
| Attribute | Type 1 | Type 2 |
| Focus | Are controls designed properly at a specific point in time | Are controls operating effectively over a period (e.g. 3–12 months) |
| Use case | Fast validation for a new process or system | Full assurance over sustained control operation |
| Time duration | Weeks to a few months | Several months to a year (depending on audit period) |
| Buyer preference | Sometimes accepted, especially early stages | More trusted by enterprise clients |
Why SOC 2 Matters in 2026?
SOC 2 Compliance Certification matters a great deal in 2026. Here’s why –
1. Demand from U.S. & Global Buyers
European firms increasingly face procurement checklists that demand SOC 2 reports. A soc 2 type 2 certification signals that you meet U.S. standard trust controls, giving your buyers confidence in cross-border security.
2. More Detailed Assurance Than Many Certifications
Compare this: ISO 27001 gives you a certified ISMS, but its audit is often summary-level and periodic. SOC 2’s attestation dives into your actual control operation and evidence testing.
3. Signals Operational Maturity
Soc2 certification is a way to prove not just that you have policies, but that they work over time. This distinguishes startups with sloppy checks from organizations that reliably enforce them. Buyers will require ongoing assurance in 2026, and not a single audit.
Reach out to learn more about SOC 2 compliance steps, technical controls, and related pentesting activities.
Need SOC 2 Compliance Support? Contact us

Step-wise Guide to SOC 2 Compliance in 2026
Assuming that you have never completed the process when it comes to SOC 2 Compliance, the work to come might be complicated. That is why we have broken down the roadmap into practical steps.
Let’s take a look at how to achieve SOC2 compliance:
| Phase | Objective | Key Actions | Outcome |
| Scope | Decide which systems, teams, and data flows the audit will cover. | Map your services, assets, and customer touchpoints. Limit scope to what clients care about most. | A clear boundary that avoids unnecessary audit costs. |
| Readiness Assessment | Identify control gaps before an auditor does. | Review current policies, logging, and access controls against the five TSCs. Carry out a practice audit where possible. | A list of weaknesses and remedies prioritised. |
| Remediation | Fix missing or weak controls. | Write policies, tighten access, improve monitoring, document incidents, and assign control owners. | Evidence-ready controls and updated documentation. |
| External Audit | Engage a licensed CPA or accredited audit firm. | Provide requested evidence, walkthroughs, and management representations. | A SOC 2 Type 1 or Type 2 attestation report. |
| Continuous Monitoring | Compliance should last longer than the report. | Automate alerts, re-evaluate every quarter, and regularly update all files. | Customer trust and being ready for renewal all the time. |
SOC 2 Compliance Certification Requirements and Evidence Checklist
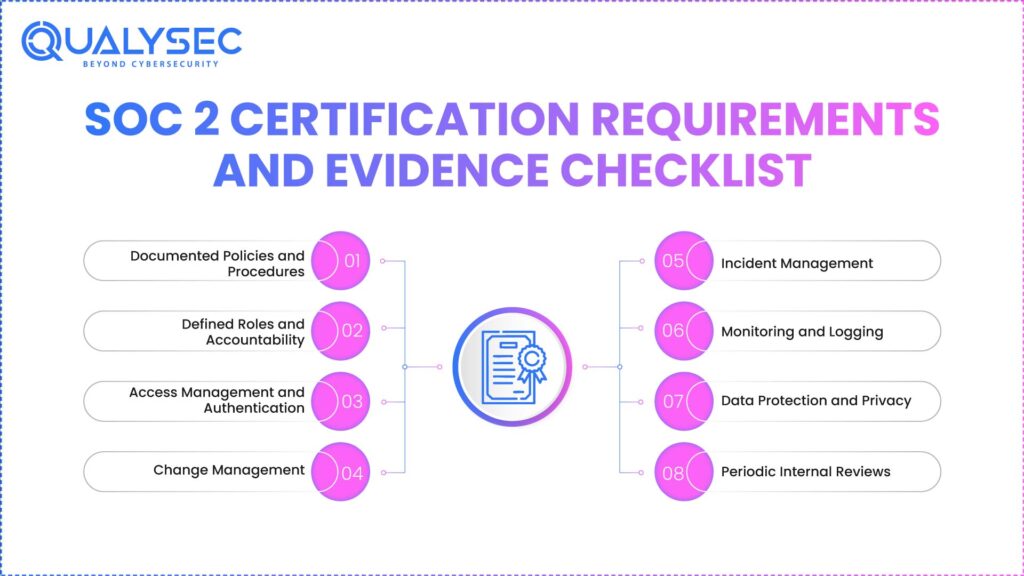
There is no official “SOC2 certification requirements checklist” from the AICPA. What exists are the criteria and expectations that auditors use to assess your environment. Without being able to demonstrate that your controls are not only well-designed but followed in the organization, a SOC2 audit will fail.
1. Documented Policies and Procedures
Auditors want to see your written evidence that security is being managed properly. This includes access controls, change management, incident response, and so on.
- Policies need to be version-controlled.
- Owners need to be clearly assigned.
- Staff must acknowledge that they have read the policies that apply to them.
2. Defined Roles and Accountability
Every control should have a person responsible for it. Auditors typically inquire about who gives approval for changes, who scrutinizes logs, and who deals with exceptions.
3. Access Management and Authentication
You need to prove you enforce the principle of least privilege.
- Show account provisioning and de-provisioning records.
- Demonstrate use of MFA and password rotation.
- Provide logs showing periodic access reviews.
Learn about Effective Threat Vulnerability Management for Cybersecurity
4. Change Management
Evidence that production changes are controlled and tested.
- Ticketing system records or pull-request histories.
- Peer-review approvals.
- Rollback documentation for failed deployments.
5. Incident Management
You should demonstrate a method that is repeatable for the detection, response, and documentation of incidents
- Incident response plan.
- Documentation of recent incidents and measures taken.
- Summaries of learned lessons and follow-up actions.
Read also: What Is Automated Threat Response & Detection?
6. Monitoring and Logging
You should have continuous visibility demonstrated by logs and alerts.
- Establish warning limits and escalation measures.
- Evidence that alerts are checked on a regular basis.
7. Data Protection and Privacy
This is essential to companies that are under the jurisdiction of GDPR or other privacy regulations.
- Encryption at rest and in transit.
- Logs on retaining and deleting data.
- Privacy notices and consent records.
8. Periodic Internal Reviews
A mature programme includes self-checks. Auditors like to see quarterly or semi-annual control reviews and risk assessments.
Download a sample SOC 2 pentesting report to review required controls, testing formats, and documentation used in compliance certification.
Get a Free Sample Pentest Report

What’s in a SOC 2 Report?
Once the SOC2 audit is complete, your organisation receives a SOC 2 attestation report from the independent CPA firm. This SOC2 reporting is the tangible proof of compliance, but it’s also sensitive and detailed, which is why most companies share it only under a non-disclosure agreement.
Speak with a Qualysec specialist to know more about SOC 2 audits!
Common Pitfalls and How to Avoid Them
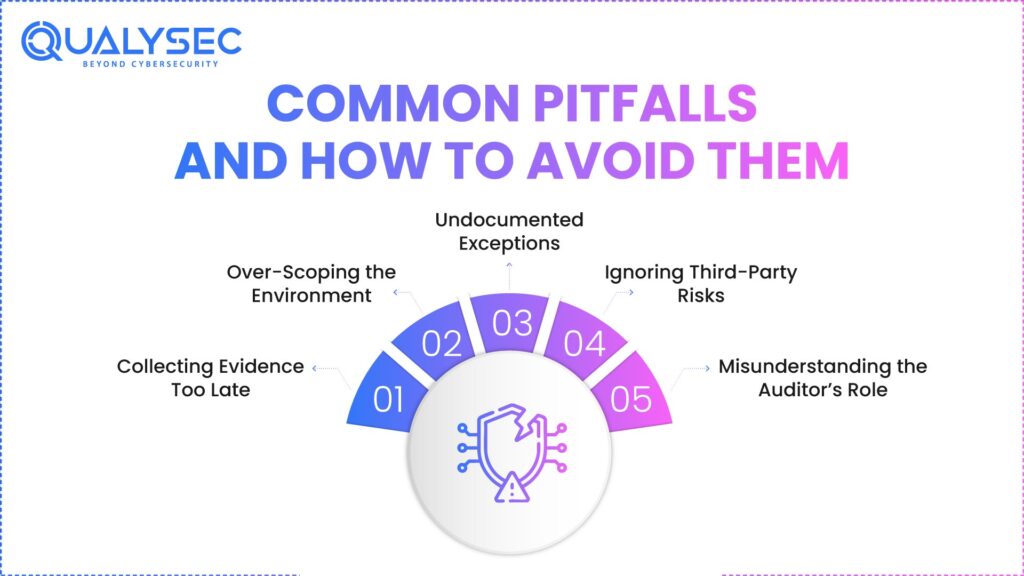
Even well-prepared teams make avoidable mistakes during SOC 2 compliance certification and audits. Here are the most common issues seen by auditors — and how to stay clear of them.
1. Collecting Evidence Too Late
Waiting until audit week to find logs or screenshots usually leads to gaps.
Solution: Collect and store evidence continuously. Automate where possible — for example, export access logs quarterly.
2. Over-Scoping the Environment
Some teams include every system in the security audit, which inflates cost and complexity.
Solution: Focus first on systems that store or process customer data. You can expand the scope later.
3. Undocumented Exceptions
Many organisations perform controls informally (e.g., security checks in Slack) but don’t record them.
Solution: Formalise those activities. A simple change-approval ticket or weekly review note counts as evidence.
Get more insights on the SaaS Security Compliance Checklist.
4. Ignoring Third-Party Risks
Vendors and hosting providers are part of your control surface.
Solution: Keep contracts, SOC 2 or ISO reports from key providers, and document your review dates.
5. Misunderstanding the Auditor’s Role
Auditors verify; they don’t design controls for you.
Solution: Use a readiness partner or internal security lead to prepare, then engage auditors only when your controls are mature.
Read our real-world case studies to learn how organizations approached security and compliance requirements.
See How We Helped Businesses Stay Secure

How Qualysec Helps You Prepare for SOC 2 Audit?
At Qualysec, we perform an extensive readiness and gap assessment. The output is a clear remediation roadmap showing where your policies or technical safeguards fall short.
After that, our experts conduct pen testing that verifies the effectiveness of your controls in real conditions. Each test follows recognised standards such as OWASP and NIST SP 800-115, providing concrete evidence.
We offer structured, audit-ready reports that map directly to SOC 2 control areas. These deliverables serve as verifiable evidence to your SOC 2 auditor.
Schedule a free consultation with our experts now!
Conclusion
Achieving SOC 2 Compliance Certification is not a box to tick. It’s a method that ensures integrity, accountability, and trust towards customers in the long run. For European companies that want to break into global markets, SOC 2 is a demand of trust that gap. It is an ISO 27001 and GDPR addition as it assures that your systems are secured, monitored, and subjected to independent auditors’ verification.
If you’re planning your first SOC 2 audit, you can partner with Qualysec. We provide top-tier SOC 2–aligned penetration testing, readiness assessments, and audit-ready documentation that give your auditor exactly what they need.
Book a 30-minute meeting to review the pentesting scope and compliance expectations.
Speak directly with Qualysec’s certified professionals to identify vulnerabilities before attackers do.
FAQs:
1. What is a SOC 2 certification?
A SOC 2 certification is given when an independent auditor examines a company’s security and operational controls and issues an attestation report. It is basically not a certificate.
2. Is SOC 2 the same as ISO 27001?
Absolutely, not! SOC 2 is an attestation that concentrates on the evaluation of the time when the controls of your organization were functioning effectively. On the other hand, the ISO 27001 is a certificate of an Information Security Management System (ISMS) that complies with ISO requirements and is usually valid to a period of three years.
3. What is a SOC 2 in the UK?
In the UK, a SOC 2 report is not issued by a UK regulator. It’s performed by an independent CPA or equivalent audit firm familiar with the AICPA framework.
4. Is SOC 2 certification mandatory?
No, SOC 2 is not legally mandatory. However, service providers are encouraged to pursue it because:
- Enterprise clients demand a current SOC 2 report during vendor selection.
- It accelerates contract approvals and investor confidence.
- It demonstrates ongoing operational maturity.
5. How much does SOC 2 compliance cost?
A SOC 2 compliance certification cost can vary depending on the size and complexity of the business, whether you qualify for type 1 or 2, etc. It can cost anywhere between lower than USD$60,000.
6. Who can certify SOC 2?
Not everybody can issue a SOC 2 attestation report. Only a licensed CPA firm (or an accredited auditor operating under AICPA attestation standards) can issue a SOC 2 report.


































































































































































































































































































































































































































































































































0 Comments