With digitalization gaining increasingly faster momentum, Cybersecurity Solutions have never been a more important issue. It is projected that the world cybersecurity market is expected to rocket, ending up at 215 billion dollars by the end of 2025 and a mind-blowing 697 billion dollars by 2035, and it grows at a yearly rate of 11.3 percent. The huge growth is being propelled by the rising cyber threat, a 17 percent year-on-year rise in the number of publicly disclosed vulnerabilities (over 30,000 last year alone), and the proliferation of AI-enhanced attacks that are more effective than the long-established defenses.
The solutions to cyber security threats are also impressive – over 3.5 million cybersecurity jobs lie vacant across the globe, which explains the necessity to adopt high-tech, automated cybersecurity tools as soon as possible. With ransomware and supply chain attacks becoming more advanced than ever, alongside the threat of quantum computing, the need to find an extensive cybersecurity solution has become mission-critical to organizations, particularly small businesses and global enterprises of all types. Read on to find out all!
What Are Cybersecurity Solutions and Why Are They Critical?
The modern hyperconnected world would be nothing without cybersecurity solutions that ensure digital safety. Fundamentally, these solutions refer to products, services, and systems that shield computer systems, networks, and sensitive information against improper access, harm, or theft. These solutions combine people, processes, and technology used to prevent, detect, and respond to cyber threats so that digital assets are secure and business processes are resilient.
Keeping You Secure
The number and advanced level of cyberattacks are increasing annually. In 2025, ransomware, phishing, insider attacks, and advanced persistent threats are the threats to organizations, and more than 43 percent of data breaches are caused by insider threats. Cybersecurity offers the required defense services against these dynamic risks.
Business Continuity
Operation downtimes, monetary loss, and reputations can be consequences of cyberattacks. Sound solutions guarantee business continuity by limiting the disruptive effects and accelerating back-on-business after an incident. This strength will be critical in keeping the confidence of customers and the expectations of stakeholders.
Regulatory Compliance
As the world becomes more stringent on data protection rules and regulations, organizations have to deal with regulations such as GDPR, HIPAA and many others. Cybersecurity solutions assist companies in putting the necessary controls and policies that would fulfill these legal requirements to avoid costly fines and legal implications.
Layered Defense
These point solutions or siloed security tools may present a vulnerability and management problems. The next-generation cybersecurity have presented consolidated platforms that equip and combine various levels of security, such as network, endpoint, application, and cloud, to offer a complete protection view and minimize blind spots.
Protection in Wide-ranging Environments
The attack surface area increases as attacks on businesses increase through cloud computing, IoT devices, and hybrid work models. Help your business give protection to cloud assets, remote endpoints, and interconnected devices with solutions to cyber security threats.
Surveillance and Quick Reaction
High-end cybersecurity AI and automation are applied in terms of real-time threat detection, around-the-clock monitoring, and automatized incident response. This minimizes the time and effectiveness of breaches and helps organizations to react fast and efficiently.
Risk Management and Governance
Cybersecurity promote risk evaluation, vulnerability management, and management frameworks. They assist companies to scan, rank, and eliminate risks and make sure security regulations are applied and standards are kept throughout the business.
Security for Small Business
Cybersecurity solutions for small business provide low cost, readily implemented defenses to allow them to protect themselves against the same threats that are targeted at larger businesses. This equalizes the competition and makes sure that even the resource-constrained organizations can result in strong security.
Latest Penetration Testing Report

Core Components of an Effective Security Solution
- Network Security – Ensures the integrity and viability of the IT security solutions against firewalls, intrusion detection/prevention, and segmentation.
- Security Awareness & Training – Trains the employees on how to be aware of phishing and social engineering attacks and other prevalent attack vectors.
- Incident Response & Management – Offers formal procedures of identifying, isolating and cleaning up security breaches.
- Data Encryption – Data at rest and in transit are kept confidential and secure against unauthorized access by sensitive information.
- Endpoint Protection – Protects devices (laptops, mobiles, IoT) with antivirus, EDR (Endpoint Detection and Response), and device management.
- Governance & Compliance – Maps security practices to regulatory requirements (GDPR, HIPAA, etc.) and deploys policies across an organization.
- Identity & Access Management (IAM) – Manages access of users to systems and data, applying least-privilege principles.
Types of Cybersecurity Solutions: A Deep Dive
The cybersecurity space is extremely broad, with many classes of solutions that are designed to fit particular threats and environments:
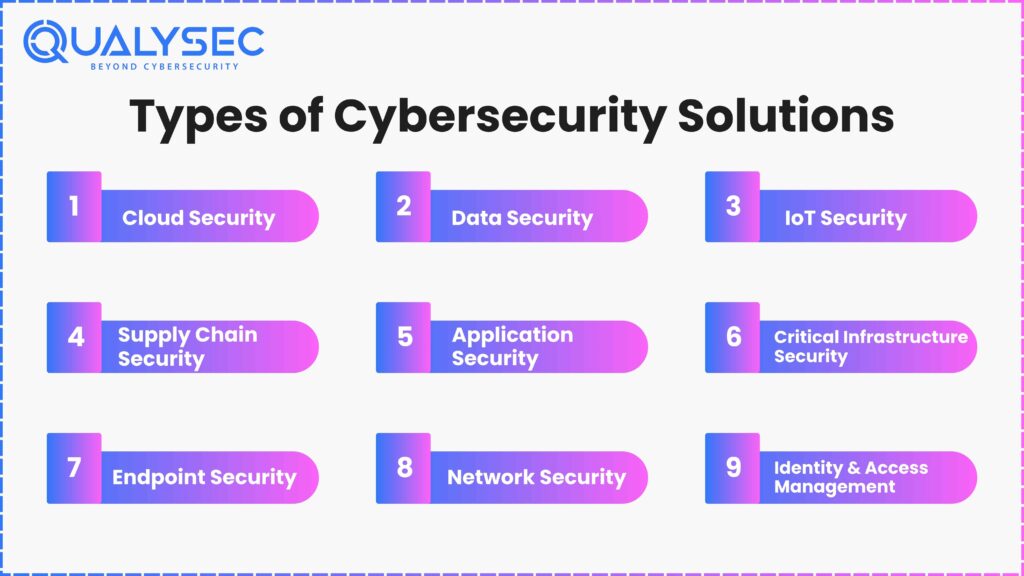
- Cloud Security: protects cloud assets and services, dealing with such risks as misconfiguration, unauthorized access, and data leakage.
- Data Security: Is concerned with keeping, confidentiality, integrity, and availability of the data, through DLP (Data Loss Prevention), encryption, and access controls.
- IoT Security: Uncovers the peculiar vulnerabilities of connected devices, provides secure firmware and patch management, and device authentication.
- Supply Chain Security: Eliminates the possibility of attacks by third-party vendors and partners and is concerned with the concept of rounds-the-clock monitoring and risk assessment.
- Application Security: Secures software and web applications against vulnerabilities and exploits, via code reviews, penetration testing, and runtime protection.
- Critical Infrastructure Security: Protects critical services (energy, transportation, healthcare) against targeted assaults, which frequently entail legacy systems.
- Endpoint Security: Protect devices against malware, ransomware, and unwanted access, with EDR/XDR platforms and mobile security solutions.
- Network Security: Firewalls, VPN, intrusion prevention systems and network segmentation are provided to disallow unwanted traffic.
- Identity & Access Management: Identity management, authentication and authorization, and user lifecycle, including MFA (multi-factor authentication) and SSO (single sign-on).
Read our recent articles on Application security testing, IoT Security, and Cloud security services.
Comparison of Major Cybersecurity Solution Categories
| Solution Category | Primary Focus | Typical Use Cases | Key Technologies | Best For |
| Application Security | Protecting apps/data | Web apps, APIs, SaaS | WAF, SAST, DAST, RASP | All orgs with custom apps |
| Cloud Security | Securing cloud assets | IaaS, PaaS, SaaS environments | CSPM, CASB, IAM, encryption | Cloud-first businesses |
| Network Security | Defending network traffic | Enterprise networks, remote access | Firewalls, VPN, IDS/IPS | All organizations |
| Endpoint Security | Device protection | Laptops, mobiles, IoT | EDR, MDM, antivirus | Distributed/remote workforces |
| Data Security | Safeguarding information | Databases, file servers, emails | DLP, encryption, backup | Regulated industries |
| Identity & Access Mgmt | User access control | Internal/external user management | IAM, MFA, SSO | All organizations |
| IoT Security | Connected device defense | Smart devices, sensors, wearables | Firmware mgmt, network seg | Manufacturing, healthcare |
| Supply Chain Security | Third-party risk | Vendor management, procurement | Continuous monitoring | Large enterprises |
How to Choose the Right Cybersecurity Solution
- Evaluate Your Risks – Determine the highest value assets of your organization and the largest threats as well. Small businesses can focus on IT security solutions and cloud security, whereas enterprises might require advanced IAM and supply chain protection.
- Think Regulatory Requirements – Make certain that solutions are equipped in relation to business industry relative standards and regulatory requirements.
- Consider Integration & Scalability – Select solutions that will be compatible with your current infrastructure and which can be scaled to match business expansion.
- Automation and AI – As talent is hard to find, and the number of attacks is increasing, automation and AI-based tools are necessary to achieve quick detection and response.
- Demand Integrated Consoles – The discreteness of security devices can result in blind areas. Consolidated systems offer improved visibility, simplified control and enhanced total defense.
- Test and Validate – Penetration testing and security assessments should be performed on a regular basis to discover gaps and confirm the efficacy of your solutions.
In the case of cybersecurity solutions to small business, pay attention to simple-to-implement, affordable tools that can provide robust protection without saturating the internal resources.
Qualysec’s Security Solutions
Qualysec Technologies provides complete cyber security solutions that considers the changing requirements of the businesses in 2025. As an organization with many years of experience, Qualysec focuses on process-based penetration testing of web applications, SaaS applications, and cloud environments to make sure that the most severe vulnerabilities are discovered and addressed before they could be used by attackers.
The salient points about the cybersecurity offerings by Qualysec are –
- Penetration Testing – Our Certified Ethical Hackers will aggressively test your systems to the highest molecule, identify obscure risks and give you practical knowledge.
- Cloud Security Assessments – Expert testing of multi-tenant SaaS application architectures, API security, and data isolation, protecting your cloud services via the latest attack vectors.
- Full Reporting – Prioritized findings with concise remediation steps, comprehensive reporting enhances business to improve its security stance in an efficient manner.
- Continuous Improvement – Postincident support and retesting is done to make certain that security measures are operational in light of new threats.
- Tailored – Qualysec solutions are designed to fit any company, whether you need cybersecurity solutions for small business or a Multinational Corporation. We offer the appropriate defense posture against cyber-attacks, fully integrated and automated.
With the ingenious support of cybersecurity solutions offered by Qualysec, organizations will have the opportunity to safely sail through the murky waters of threats in 2025, with business continuity, compliance, and customer confidence.
Talk to our Cybersecurity Expert to discuss your specific needs and how we can help your business.
Conclusion
Organizations, especially small businesses, can sufficiently secure themselves against sophisticated cyber threats by getting acquainted with the Cybersecurity Solutions, types, and strategic selection of cybersecurity products. Qualysec Technologies is an ideal partner to rely on since it provides customized all-round security services that give business organizations a competitive advantage over attackers. The only way to establish effective cyber defense and protect your assets as well as the trust of your customers in 2025 and onward is to adopt these best practices and use the expertise to your advantage. Contact us today to get started!
Frequently Asked Questions (FAQs)
1. What are cyber security threats?
Cybersecurity threat refers to harmful practices that attack digital systems, networks, and information. Those are malware, ransomware, phishing, DDoS, insider threats, and advanced persistent threats (APTs). The adversaries constantly modify the threat environment through the use of AI, IoT exploitation, and cloud attacks.
2. What is the most common type of cybersecurity solution?
The most widely adopted cyber security solutions are firewalls and intrusion prevention systems, which are network security solutions. Nevertheless, endpoint security, cloud security, and identity management are becoming more widespread as companies have to adjust to remote work and cloud migration.
3. What is the difference between cybersecurity and network security?
Cybersecurity is a broad subject and refers to all the processes involved in protecting digital resources against cyber threat, which may include data, applications, and devices. Network security is a subfield of cybersecurity specifically concerned with the integrity, confidentiality and the availability of information across the networks.
4. How much do cybersecurity solutions cost?
Prices are highly flexible depending on the size of the organization, complexity of the solution, and requirements of the regulations. Small companies may pay a couple of thousand dollars per year to protect their business with necessary cybersecurity tools, whereas big corporations can afford millions of dollars to buy state-of-the-art unified platforms. The dynamism in the global market is expressed in the form of growing investment in all sectors.
5. What is a cybersecurity platform?
A cybersecurity platform is a unified system of tools and services that targets the protection of digital assets through integrated threats detection, prevention, and response. Platforms, centralized management, automation, and analytics are realized with platforms, which reduces complexity and increases an security posture.



























![Top 20 Network Security Companies in USA [2025 Updated List]](https://beta.qualysec.com/wp-content/uploads/2025/05/Top-20-Network-Security-Companies-in-USA-2025-Updated-List-scaled.jpg)











































































































































































































































































































































































































































































0 Comments