Cloud security posture management is essential for modern businesses, as cloud adoption has grown to be a defining feature. To operate applications, store sensitive data, and provide real-time client support, teams in the United States and all around now depend on cloud architecture. But security threats increase at the same rate as more businesses move to hybrid settings, AWS, Azure, Google Cloud, and other systems. Most cloud breaches are no longer caused by clever exploits or sophisticated threat actors. Often, they result in one preventable problem: misconfiguration. Millions of documents may be exposed without anyone noticing from a single open storage bucket, lax access rule, or forgotten encryption setting.
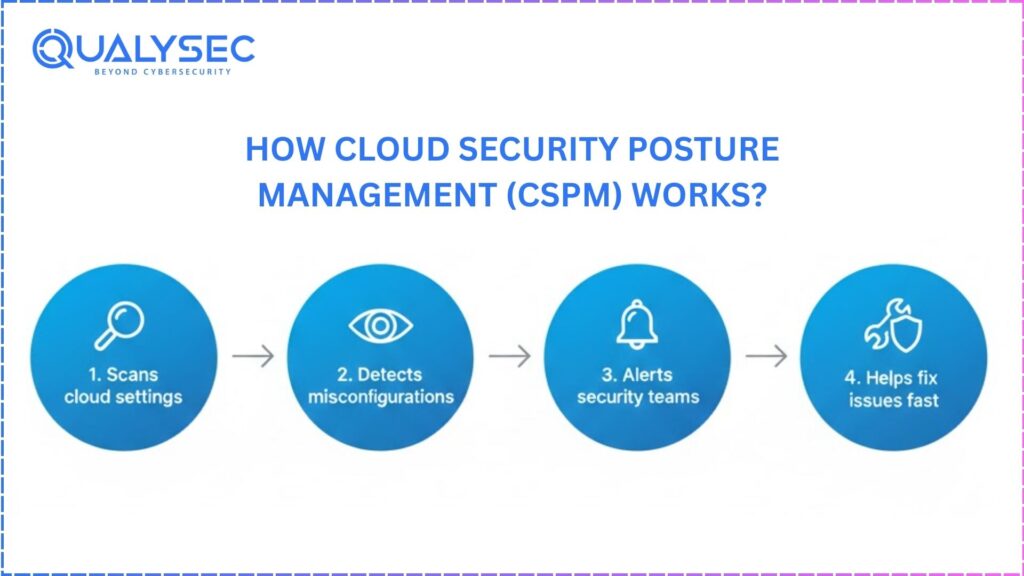
One of the most vital strategies for reducing these hazards is cloud security posture management (CSPM). It enables businesses to routinely inspect their cloud configurations, find errors, apply rules, and match with compliance standards. Given that companies almost every day add to their cloud environments, manual audits are not adequate anymore. CSPM enables teams to prevent expensive errors by providing constant monitoring, automatic security checks, and transparent visibility into multi-cloud installations. CSPM is vital for creating a safe basis fit for scaling as cloud complexity grows.
What is Cloud Security Posture Management (CSPM)?
Cloud Security Posture Management is the synergy of methods and tools aimed at constantly tracking and enhancing the security setup of cloud systems. It emphasizes finding compliance flaws and hazardous settings that might cause breaches. Cloud assets increase quickly as companies expand, opening up numerous chances for misconfigurations. CSPM provides teams with a real-time view of their cloud security posture, therefore helping to avoid these errors.
Weak access controls, unsafe network rules, missing encryption, and policy breaches are all examined in the cloud infrastructure by a CSPM solution. It points out vulnerable places and clarifies how to fix them before attackers use the flaw. Because cloud environments are dynamic, CSPM solutions scan frequently instead of doing one-time audits. This guarantees that any variation from secure baselines is immediately detected.
Because CSPM helps to improve multi-cloud security posture, many businesses use it since it accommodates AWS, Azure, Google Cloud, Kubernetes, and hybrid systems. Most companies now use two or more cloud platforms; hence, unified visibility becomes imperative. CSPM is the main system that monitors all assets, approvals, and configurations across domains.
If you want help reviewing your cloud posture, Qualysec provides detailed cloud misconfiguration assessments. Schedule a consultation now!
Why CSPM Matters For The USA and Global Companies?
For worldwide operations, businesses in the United States must follow stringent legal rules, including HIPAA, PCI DSS, NIST CSF, FedRAMP, SOX, GLBA, and GDPR. One wrong setting in a cloud database or storage solution can result in significant legal breaches. Penalties for such errors can be harsh, and many businesses only learn of them after a breach. Through constant monitoring and automated compliance checks tailored to international standards, CSPM aids in the prevention of these problems.
CSPM has become critical as cloud adoption grows in worldwide marketplaces. Many companies regularly use many teams to deploy resources. Particularly when cloud systems grow fast, security teams sometimes find it difficult to match the rate of deployment. Offering real-time stance tracking, Cloud misconfiguration detection tools, and automated security scanning helps CSPM bridge this divide. This stops misconfigurations that inevitably occur during rapid-paced development.
By providing centralized visibility, CSPM relieves the strain on security personnel. The CSPM tool immediately alerts teams when anything breaks policy instead of having to manually check every new storage bucket, IAM role, or network setup.
Get Expert Help Securing Your Cloud →

Core Competencies of CSPM Applications
More than simple warnings are offered by a powerful cloud security posture management strategy. Modern CSPM systems integrate policy controls, automated analysis, remediation advice, and CSPM compliance monitoring to offer comprehensive cloud security policy enforcement. The basic characteristics you should anticipate are detailed here.
1. Detecting Cloud Configuration Mistakes
Every CSPM solution starts with misconfiguration identification. These instruments search cloud environments for dangerous settings and arrangements that might compromise valuable assets. They identify, for instance, openly available storage buckets that an attacker might scan and use. Additionally, they highlight IAM roles with too many privileges that might be abused in a breach. This tool is always searching for problems, including poor authentication rules and missing encryption settings.
Team members may fix security flaws before attackers discover them with Cloud misconfiguration detection tools. Rather than finding problems throughout an audit or after an accident, CSPM solutions show them in real time. Early identification helps to keep systems in compliance with security CSPM best practices, automation and lowers the possibility of data loss.
For a deep cloud misconfiguration analysis, consider Qualysec’s cloud VAPT services!
2. CSPM oversight of conformity
For businesses running under tight rules, CPSM compliance monitoring is vital. CSPM systems connect cloud settings to standards, including ISO 27001, NIST, SOC 2, HIPAA, PCI DSS, GDPR, and CIS Benchmarks. CSPM technologies automatically check compliance alignment and draw attention to outliers instead of manually reviewing every control.
Speed and accuracy define the advantages of automated compliance inspections. Teams no longer rely on yearly audits or hand assessments. Real-time compliance dashboards and alerts are produced by CSPM any time something moves out of orientation. This enables businesses to show auditors consistent compliance, keep excellent documentation, and avoid fines.
Access the Complete Cloud Compliance Guide →
3. Cloud Security Policy Enforcement
This CSPM feature guarantees that security policies are always followed across the company. Policy implementation stops the production of resources in perilous configurations. CSPM will, for instance, block or flag any resource that goes against your policy need for encryption at rest. This lowers the possibility of human error and guarantees business-wide alignment.
Policy enforcement assures teams that all missions meet security criteria. Automated systems stop misconfigurations before they happen as settings grow. This lowers the burden on security teams and makes cloud environments safer.
4. Management of multi-cloud security posture
Most businesses today use multi-cloud configurations to guarantee performance, redundancy, and flexibility. But managing AWS, Azure, Google Cloud, and private cloud environments manually becomes overwhelming. CSPM tools solve this by providing a single dashboard showing the security posture for every cloud platform.
Multi-cloud posture control helps find hidden assets, spot configuration drift, and ensure uniform policies across several systems. This guarantees teams keep visibility even when cloud networks become more complicated and lessens blind areas.
Discover our recent article about What Is Multi-Cloud Security? Challenges and Best Practices.
Common Cloud Hazards CSPM Addresses
Strong security measures abound in cloud settings, yet misusing or incorrectly setting them might introduce serious flaws. CSPM offers remedies for several high-risk problems that frequently result in breaches.
- Incorrect Settings: Cloud breaches are most often brought on by misconfigurations. This includes unlocked databases, public storage buckets, limited IAM permissions, and disabled encryption. These errors are actively sought by attackers; hence, fast detection is vital. CSPM keeps an eye on setups so no mistake goes missed.
- Lack of Visibility: Particularly in multi-cloud arrangements, cloud environments quickly turn complicated. Many groups forget about shadow deployments, resources, and systems that are forgotten. Visibility is centralized by CSPM so teams can view everything in one location and prevent blind spots that attackers might use.
- Compliance Deficiencies: Manual compliance inspections are sluggish, erratic, and vulnerable to human error. CSPM tools simplify regulatory audits and lower the likelihood of violations by automating compliance verification.
CSPM Vs Traditional Security Tools
Traditional security tools like firewalls, antivirus programs, and SIEM platforms are necessary, but they were not built for cloud native environments. CSPM fills the gap by focusing on configuration and policy-based risks.
| Feature | Traditional Tools | CSPM |
| Multi cloud visibility | Limited | Complete, unified dashboard |
| Misconfiguration detection | No | Yes, continuous |
| Compliance monitoring | Manual | Automated |
| Policy enforcement | Basic | Strong and customizable |
| Multi-cloud visibility | Slow | Immediate posture change alerts |
CSPM Best Practices Automation
One of the major advantages of CSPM is automation. It quickens remediation, increases consistency, and lowers manual effort. The following are more ideal methods that enable teams to develop a solid cloud security stance.
I. Automate correction procedures.
Automated remediation lets CSPM instruments solve some problems immediately. This includes blocking public access to resources, correcting IAM policies, enabling encryption for storage services, or closing open ports. Automating these solutions guarantees fast reaction times and lowers human error.
II. Connect CI/CD pipelines with CSPM.
Integrating CSPM into CI/CD pipelines guarantees that security inspections precede deployment. This avoids incorrect settings from getting to production systems. Early in the process, developers get rapid input that helps them to address problems.
III. Implement Policy as Code.
Policy as code lets teams keep cloud security policies in versioned configuration files. This enables automated, consistent, and repeatable enforcement. It also assists teams in working on security policies and following changes over time.
IV. Automate Compliance Papers.
During audits, CSPM systems provide dashboards and exportable reports demonstrating conformity with standards, including ISO 27001, SOC 2, NIST, HIPAA, and PCI DSS, hence saving hours of manual labor.
CSPM for Multi-Cloud Security Posture
Although multi-cloud environments offer flexibility, they also introduce complexity. CSPM helps reduce complexity by enabling consistent policy controls and consolidated visibility.
Hidden or deserted assets found throughout AWS, Azure, Google Cloud, and Kubernetes clusters are discovered by CSPM instruments. They identify weak configurations, assess risks, and apply consistent security rules across settings. This guarantees teams can monitor everything from one spot and so avoid configuration drift.
If you want a multi-cloud posture review, Qualysec offers full assessments with actionable reports!
How CSPM Assists With Regulatory Compliance
Driving adoption of CSPM is mostly about regulatory compliance. Through constant control mapping, CSPM solutions enable businesses to stay aligned with frameworks.
Instead of depending on yearly or quarterly inspections, they offer immediate visibility of compliance. CSPM solutions notify teams as soon as a setup falls out of compliance. By producing computerized compliance logs, they also assist with evidence gathering and audit readiness.
Choosing The Best CSPM Solution
Choosing the best CSPM platform calls for an assessment of the capabilities most suited for your business.
- Reach: Make sure your CSPM solution supports hybrid configurations as well as AWS, Azure, Google Cloud, and Kubernetes. The tool has to change as your surroundings expand.
- Automated Capabilities: A robust CSPM platform lowers manual effort by providing policy enforcement, automated remediation, auto alerting, and compliance reporting.
- Integration Alternatives: The tool should work with CI/CD pipelines, SIEM systems, IAM systems, and DevOps procedures. Smooth integration enhances operating efficiency and security.
- Threat Detection Exactness: CSPM should draw attention to actual misconfigurations and reduce false positives so teams concentrate on problems that are actually important.
- User friendliness: Teams may monitor posture rapidly and make educated decisions free of uncertainty with a clean dashboard and simple processes.
Explore: Top Cloud Security Solutions: Challenges, Trends, and Best Practices
How Qualysec Helps Strengthen Your Cloud Security Posture
- With thorough manual validation, Qualysec detects cloud misconfigurations across AWS, Azure, GCP, and hybrid configurations so you don’t rely only on automated scans.
- Their cloud penetration tests draw attention to dangerous access controls, exposed workloads, faulty IAM configurations, and policy drift before attackers take advantage of them.
- By matching your surroundings with frameworks like SOC 2, ISO 27001, GDPR, HIPAA, and PCI DSS, we can help you preserve your multi-cloud security position.
- Qualysec’s consulting team helps you with best practice policy enforcement, step-by-step solutions, and customized pragmatic cloud hardening advice depending on your surroundings.
- Through professionally conducted evaluations, you also get support for continuous monitoring, remedial direction, and enhancement of your general cloud security policy enforcement.
Discover gaps in your cloud security. Get a free audit →
Speak directly with Qualysec’s cloud security experts to detect misconfigurations before they expose your cloud environment.
Conclusion
For companies operating in the cloud, cloud security posture management has become necessary. Companies cannot rely on manual assessments or conventional tools since misconfigurations keep resulting in significant breaches. CSPM offers real-time compliance insights, strong policy management, automated detection, and continual monitoring. Even as cloud systems grow swiftly across many platforms, they keep their secure nature.
With a strong CSPM foundation, businesses may confidently scale cloud activities, reduce risks, and maintain legal compliance. As conditions change to become more dynamic and complex, CSPM ensures your cloud stance is stable, resilient, and secure.
If you want expert help strengthening your cloud posture and eliminating misconfigurations, you can explore Qualysec’s cloud security services anytime!
FAQS
1. What is Cloud Security Posture Management (CSPM)?
CSPM enables policy implementation, correction of cloud misconfigurations, and harmonization of cloud systems with compliance frameworks. By giving unified visibility, it enables a multi-cloud security attitude.
2. What should I look for when choosing a CSPM solution?
Look for integration simplicity, a user-friendly dashboard, multi-cloud support, automation features, and threat detection accuracy.
3. How does CSPM differ from traditional security tools?
Traditional instruments track networks or endpoints; CSPM emphasizes cloud setup, posture management, misconfiguration detection, and CSPM compliance monitoring.
4. How can CSPM help with regulatory compliance?
CSPM automatically generates audit-ready compliance reports and maps cloud configurations to drift warnings, alert systems, and compliance frameworks.
5. What are the core capabilities of CSPM tools?
Among important features are real-time warnings, automatic correction, policy enforcement, multi-cloud visibility, CPSM compliance monitoring, and misconfiguration detection.







































































































































































































































































































































































































































































































































































































0 Comments